Aviationshop.com Scam: Unmasking the Web of Deceit

Aviationshop.com Scam: Overview
Aviationshop.com, despite its seemingly legitimate facade, is not the online haven it pretends to be. Instead, it stands as a testament to the pervasive issue of fake online websites, masterfully crafted by scammers with the sinister intent of duping unsuspecting customers.
Setting up fake online stores has become an alarmingly easy task for scammers. Armed with access to a computer system and the internet, anyone can create a deceptive platform under any name, creating a playground for fraudulent activities. Aviationshop.com, like many others, operates under the guise of a genuine website, enticing users into making purchases that could lead to dire consequences.
One common tactic employed by scammers is brand impersonation. They mimic well-known brands, replicating entire website designs and adopting similar URLs to deceive customers into believing they are on a legitimate site. This form of phishing attack, known as brand impersonation, adds a layer of authenticity to the scam, making it more challenging for users to discern the deception.
The risks associated with customers falling victim to fake websites like Aviationshop.com are multifaceted. Scammers may have various intentions, ranging from relatively small risks to potentially catastrophic outcomes. These malicious actors may aim to steal personal information such as names, addresses, or phone numbers, subsequently selling this data in bulk on the dark web.
More nefariously, scammers may target banking information or credit card details to commit fraud or initiate unauthorized fund transfers. The sale of counterfeit or non-existent products further compounds the issue, leaving customers empty-handed and frustrated. Additionally, some scammers engage in brand impersonation with the deliberate intention of damaging a legitimate business’s reputation.
In essence, Aviationshop.com and its ilk serve as cautionary tales in the online realm. Customers must exercise vigilance, scrutinizing websites for authenticity and ensuring that personal and financial information is shared only with trusted entities. The prevalence of fake online shopping sites underscores the importance of cultivating a skeptical eye to navigate the digital landscape securely.
How can we define a fraudulent online shopping site?

Scammers set up fake online stores that may appear genuine, but their real aim is to trick you into giving away your money, passwords, or personal information.
They use various tactics to get people to visit these fraudulent sites. Some folks may stumble upon them accidentally while browsing the internet, but scammers often rely on phishing scams. They send fake emails, texts, or social media ads to lure in unsuspecting visitors.
These fake stores can look very convincing, mimicking the appearance of well-known retailers. They use familiar logos, stolen images, and web addresses that are similar to the real ones. To an average person, these sites seem safe.
What makes them attractive is the incredible deals they offer. You’ll find luxury items like clothing, jewelry, and electronics from top brands at a fraction of the usual price. They even promise free shipping and super-fast delivery, making the deals even more tempting.
Notably, these scams are more common during the holiday season and big shopping events when people are looking for great deals and quick delivery. So, it’s important to stay cautious and double-check before making any online purchases to avoid falling victim to these fraudulent websites.
In what ways fake online stores deceive customers?

Scammers put a lot of work into making their fake online stores look like real ones. Here’s how they carry out these shopping scams:
Building the Fake Website
Criminals start by registering a web address that’s strikingly similar to a legitimate retailer’s site. They might use typos or add extra words (like “walmarkt.com” or “walmartsavingsonline.com”). The fake site is then designed to mimic the real store in every way possible. They copy the official company’s design, logos, branding, product photos, and more to make it seem authentic. They even use brand names, images, and trademarks without permission to create an air of credibility. The site has all the features of a genuine store, like shopping categories, product pages, a cart, and a checkout that all work just like the real thing.
Attracting Victims with Social Media Ads
Scammers heavily promote their fake sites on platforms like Facebook, Instagram, and others by paying for ads. These ads promise deals of up to 90% off, flash sales, clearance items, and other fake discounts to draw in shoppers. But when people click on these ads, instead of going to the real store’s site, they end up on the scam site. The goal is to keep victims within the fraudulent site.
Taking Payments but Not Delivering Orders
On the fake site, users can browse products, add items to a cart, and enter their payment and personal information during checkout. Shoppers have to provide their full name, address, phone number, credit card details, and other sensitive information. But here’s the catch: no real products are ever sent out. Once payments go through, the orders simply vanish into thin air.
Stealing Personal and Financial Data
In addition to grabbing payment data, the scammers also collect all the personal information users provide on the site. This includes names, addresses, and contact details. Moreover, they snatch up credit card numbers, CVV codes, and expiration dates for fraudulent purposes. This stolen data is either employed for identity theft or sold on dark web marketplaces to other internet crooks. In many cases, email addresses are added to scam mailing lists for phishing campaigns.
Creating these devious fake stores takes a lot of time and effort. It’s crucial to understand their sneaky tactics to avoid falling victim to their scams.
Indicators that an E-Commerce Website is Not Legitimate

Even though scam websites try to look real, if you take a closer look, you can spot signs that they’re fake:
- No Contact Info: They won’t give you a phone number, email, or physical address for customer service.
- Stock Photos: Instead of showing real product pictures, they use images taken from other websites.
- No Social Media Presence: Legit brands have official social media accounts, but scams won’t.
- Checkout Errors: You’ll run into problems or glitches when you try to buy something.
- Copied Legal Pages: The “Terms of Service” and “Privacy Policy” look like they’ve been copied from somewhere else.
- Odd URLs: The web address might have strange typos or extra words, like “walmarkt.com.”
- Too-Good-To-Be-True Discounts: They offer deals that are just way too amazing, like up to 90% off or even more.
- Poor Quality: The website might have lots of mistakes, like bad grammar, typos, and messy design.
- Only Positive Reviews: You’ll see hundreds of generic 5-star reviews, which is a big red flag.
- No HTTPS: The web address doesn’t have “https” and a padlock icon, which means the site isn’t safe and secure.
- No Business Details: The website won’t tell you anything about who owns or runs it.
When you see a bunch of these signs all together, it’s pretty clear that the website is not trustworthy. So, be really careful about giving them any of your personal information because it’s likely a scam.
Guidelines for Safe Online Shopping and Protecting Against Scams

In today’s digital age, online shopping has become increasingly popular, but it’s also given rise to e-commerce scams. To protect yourself when shopping online, there are several precautions you can take.
Firstly, when you visit a website, look for their contact information, which should include a phone number and a physical address. Reputable sites will prominently display this information, and they should also provide customer service options for your inquiries and concerns.
Secondly, if you come across an unfamiliar online store, it’s wise to do some quick research. Simply search for the site’s name and check for reviews, scam reports, and feedback from other customers. This can help you gauge the site’s legitimacy.
Another important step is to verify the website’s URL. Make sure it matches the official domain of the company you intend to shop from. Be on the lookout for any typos or extra words in the URL, as these can be indicators of fraudulent sites.
Moreover, always check the security of the website. Ensure that it has full HTTPS encryption and a padlock icon during the checkout process. This helps protect your personal and financial information from being intercepted by malicious actors.
It’s also a good practice to avoid clicking on store ads on social media platforms. These ads can often lead to scam sites. Instead, go directly to the official websites of known and trusted companies.
When making online purchases, use credit cards rather than direct wire transfers. Credit cards provide an extra layer of security, and if you encounter fraudulent charges, they are easier to dispute.
Never wire money through services like Western Union or MoneyGram for online orders, as these transfers are irrevocable and can’t be undone if you fall victim to a scam.
Lastly, prioritize using strong and unique passwords for your online accounts. This can help prevent criminals from accessing your other accounts if one is compromised.
In summary, when in doubt, it’s best to err on the side of caution. If a website or online store feels questionable or “off” to you, it’s safer to avoid entering your data. There are plenty of legitimate retailers available where you can shop with confidence. Your online safety and security should always be a top priority.
How should you proceed if you’ve been scammed by a counterfeit online shopping site?

If you’ve unfortunately fallen victim to an online scam, it’s crucial to take immediate action to protect yourself and your money. Here are some simple steps you can follow:
- Reverse Payments: If you used a credit card for the transaction, ask your bank for a chargeback to try to get your money back. If you made a wire transfer, contact the recipient’s bank to see if they can reverse it.
- Report Social Media Accounts: If the scam involved social media, report the fake accounts to have them taken down. This can prevent others from falling victim to the same scam.
- Reset Passwords: Change the passwords on any online accounts that shared the same login details as the one you used for the scam site. This helps protect your other accounts.
- Contact Your Bank: Immediately inform your bank about any disputed charges. Consider canceling your card to prevent further fraudulent purchases.
- File a Complaint: Report the scam to authorities like the Federal Trade Commission (FTC) and the Internet Crime Complaint Center. Provide any records or evidence you have.
- Keep Records: Save any receipts, emails, screenshots, and details related to the scam. These records serve as proof of the fraudulent transaction.
- Check Credit Reports: Request your credit reports to look for any accounts opened fraudulently using your information. If necessary, consider placing a credit freeze to prevent further misuse of your identity.
- Leave Online Reviews: Share your experience on consumer review websites to warn others about the scam. However, be sure not to unfairly harm legitimate businesses.
- Check for Viruses: Run a powerful antimalware scan on your device to make sure it’s not infected with any malicious software that may have come from the scam site.
By taking these steps, you can help mitigate the damage caused by falling victim to an online scam and contribute to the prevention of future scams. Remember, it’s essential to act swiftly to protect your finances and personal information.
What is the process for reporting a fraudulent online store?
If you find a fake online store, report it to Google or Microsoft. In the U.S., you can also contact the FTC or the FBI’s Internet Crime Complaint Center (IC3). When reporting, share as much info as possible about why you think the site is a scam. This helps them investigate and take action. Reporting is essential to protect others from falling for the same trick.
What are some tips for ensuring your online safety?

Staying safe online is super important. There are some simple rules you can follow to help protect your computer and your personal information from bad stuff like viruses and scams.
First, always keep your computer’s software and apps up to date. When your PC tells you there’s a new update, it’s a good idea to download and install it. These updates often have important fixes and security patches to keep your device safe.
When you’re installing new programs or apps, be very careful. Sometimes, when you’re installing something, there might be other software trying to sneak in. Read everything carefully and don’t rush. If you see something you don’t recognize or don’t want, make sure to uncheck it before clicking “Next.”
Be cautious about what you download. There are bad people out there who want to trick you into downloading harmful software. They might disguise it as something fun like a game or a useful tool. So, be sure to only download from trusted sources like official app stores.
Using pirated software, which is basically illegal copies of programs, is a no-no. It can put your computer and your privacy at risk. So, always get your software from legitimate sources.
Backing up your data is like making a copy of all the important stuff on your system. It’s a good idea to do this regularly and make sure you can restore the backup if needed. This can be a lifesaver if you ever get hit by something nasty like ransomware. Just remember not to connect the backup drive to a device if you suspect it has a virus.
Be careful where you click on the internet. Avoid clicking on links or downloading stuff from places you don’t know. Some links or attachments can hide viruses or scams. Stick to trusted websites and be cautious about emails or messages from unknown sources.
Having a good antivirus program is like having a superhero to protect your computer. It can help spot and stop bad stuff before it can harm your system. Make sure to keep your antivirus up to date so it’s ready to tackle the latest cyber threats.
Ad blockers are like shields against annoying and harmful ads. They can stop ads from websites that might try to infect your device with viruses or trick you into revealing your personal information. Using an ad blocker alongside your antivirus is a smart move.
People on the internet can be tricky, so be alert. Be careful about clicking on links or responding to messages from unknown sources. Sometimes, they might pretend to be someone you know or trust. But don’t be fooled by familiar names or numbers – always stay on your guard.
Following these basic safety rules will help you stay safe online. The internet is a fun and useful place, but it can have some dangers too. By being cautious and following these guidelines, you can protect yourself and enjoy your online experience without any unpleasant surprises.
Special Offer
In order to remove Aviationshop.com hassle free, we suggest you to scan the PC with powerful SpyHunter antimalware scanner. The fully functional free Trial of SpyHunter is Available for 7 days (Windows Version) with Credit Card required. There are no upfront charges within this period. Further, no charge will apply if you cancel 2 business days before the trail ends. For Mac Users, it is suggested to use Combo Cleaner which is a powerful antivirus and System optimizer.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
How to remove unwanted program from Windows 11
To get rid of an unsafe program on your Windows computer, follow these straightforward steps:
- Open your computer's settings by pressing "Windows + I" or right-clicking the "Start" button and choosing "Settings."

- In the settings window, click on "Apps" and then select "Apps & Features."
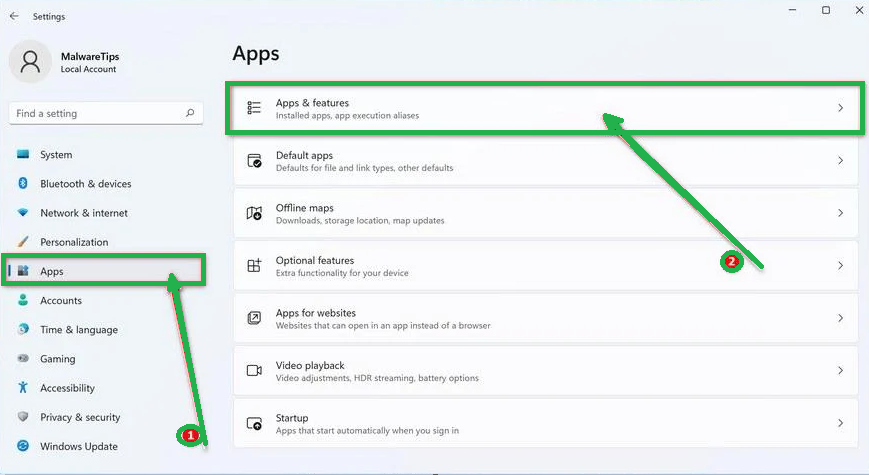
- You'll see a list of installed programs. Scroll through them and look for anything suspicious or unfamiliar. To make it easier, you can sort the list by the installation date. Just click "Sort by" and pick "Install date."
- Keep an eye out for any programs that don't seem right – things you don't remember installing or that don't sound like legitimate software. When you find a suspicious program, click the three dots next to it and choose "Uninstall."

- A message box will pop up. Confirm the uninstall process by clicking "Uninstall" and follow any prompts that come up to complete the removal.
- It's crucial to read all the prompts carefully because some malicious programs might try to sneak in extra things, hoping you won't notice.

- Once you've successfully removed the malicious programs from your computer, you've taken a big step in getting rid of the unwanted program.
How to Remove Unwanted program Virus from Windows 10
To remove an unwanted program from a Windows 10 computer, follow these steps:
- Open the "Settings" app by press the "Windows key + I" on your keyboard. Alternatively, you can click the "Start" button on the taskbar and then choose "Settings" (the gear icon).
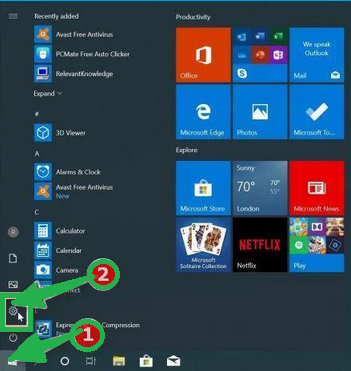
- In the "Windows Settings" window, you'll see various options. Click on "Apps." By default, it should take you to "Apps and Features," but if not, select it from the options on the left.
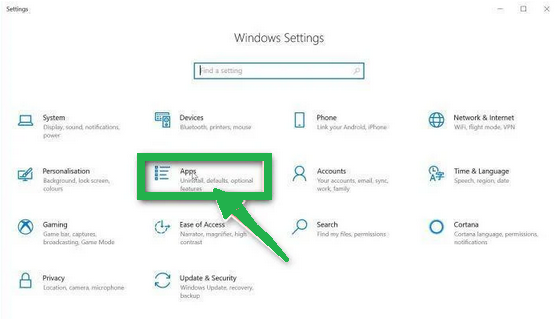
- In the "Apps & Features" settings, scroll through the list of installed programs. Look for anything that seems unfamiliar or suspicious. To help with this, you can sort the programs by their installation date. To do this, click "Sort by" and pick "Install date."
- Keep an eye out for any program that you don't remember downloading or that doesn't seem like a legitimate piece of software. When you find a suspicious program, click on it and then choose "Uninstall" from the menu that appears.

- A message box will pop up to confirm the uninstallation process. Click "Uninstall" to confirm and follow any additional prompts that come up to complete the removal.
- It's essential to carefully read all the prompts because some malicious programs might try to sneak in additional things during the process, hoping you won't notice.

- Once you've gone through these steps successfully, the malicious program will be removed from your computer.
How to Remove Unwanted program Virus from Windows 7
To remove an unwanted program from Windows 7, follow these steps:
- Click the "Start" button and select "Control Panel."
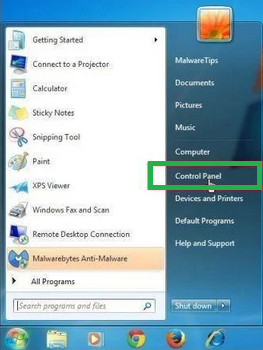
- In the Control Panel, click "Uninstall a Program" under the "Programs" category.

- You'll see a list of all installed programs in the "Programs and Features" screen. Find any suspicious or unfamiliar programs, click to highlight them, and then click "Uninstall."
- Look for anything that doesn't seem legitimate or you don't remember installing.

- Confirm the uninstallation in the message box by clicking "Yes" and follow any prompts to complete the removal. Read carefully, as some malicious programs try to slip in unnoticed.
- Once you've completed these steps, the malicious software will be removed from your computer.
How to Remove Unwanted program from Android/Mobile
To remove an unwanted program virus from your Android phone, follow these simple steps:
Step 1: Start in Safe Mode
First, we'll start your phone in Safe Mode. Safe Mode boots your Android with only the essential apps and settings, preventing malicious apps from interfering.
- Long-press your phone's power button (usually found on the side of your phone) until the power off menu appears.
- When the menu appears, tap and hold the "Power off" button on your screen. You'll see a "Safe mode" option.

- Tap on "Safe mode" to enter it.

- Your phone will restart in Safe Mode, and you'll see the "Safe Mode" text at the bottom left corner of your device.

If you can't find Safe Mode on your phone, you can activate Airplane mode instead to cut off network connections.
Step 2: Check for Malicious Apps with Administrator Privileges
In this step, we'll check if there are any malicious apps with administrator privileges on your phone. These privileges are sometimes used for legitimate purposes but can also be exploited by malicious apps to prevent their removal.
- Tap the "Settings" app on your phone's menu or home screen.
- In the "Settings" menu, look for "Biometrics and Security" (or similar) and then navigate to "Other Security Settings" and "Device admin apps." The location of this option may vary depending on your Android version or phone brand.
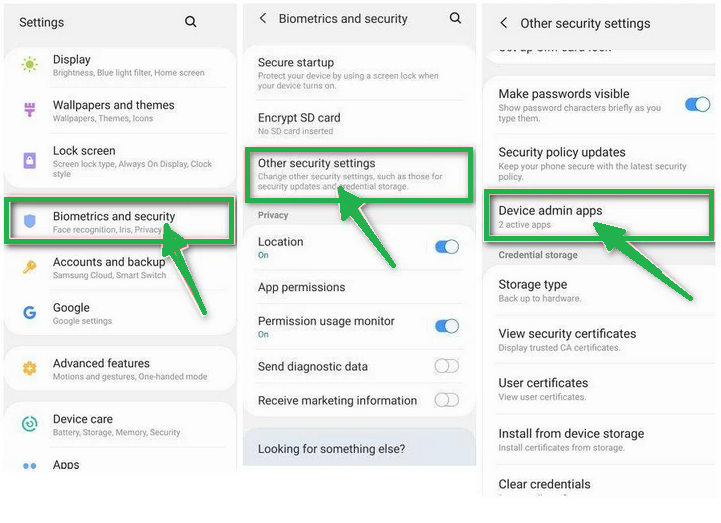
If you can't find "Device admin apps" easily, you can use your phone's search function to look for it.
- Once you're in the list of device admin apps, disable admin rights by tapping the option next to the app. This will remove the checkmark or turn off the toggle button. Some phones also let you tap the app in the admin apps list and then use the "Uninstall" link to remove it immediately.
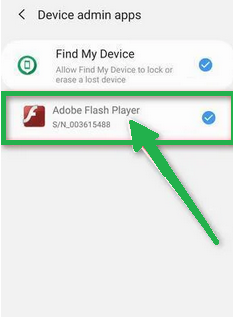
Step 3: Check for Malicious Apps
While your phone is still in Safe Mode, we'll check for malicious apps.
- Tap the "Settings" app.

- In the "Settings" menu, tap on "Apps" or "App Manager" to view all installed applications on your phone.
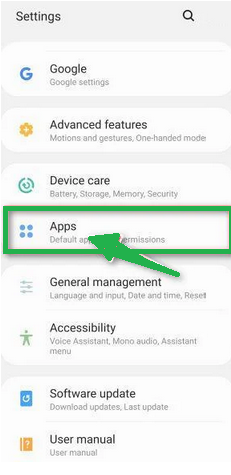
- You'll see a list of all installed apps. Scroll through the list and look for any suspicious apps that you don't remember downloading or that don't seem genuine. Malware is often hidden in apps like photo editors, weather apps, or camera apps.
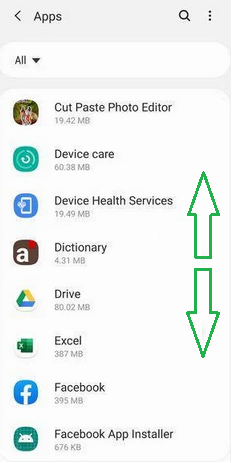
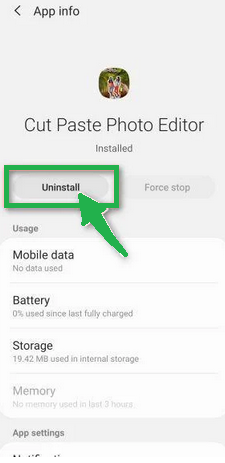
- When you find a suspicious app, tap on it to uninstall. This won't open the app but will take you to the app details screen. If the app is currently running, tap "Force stop," then tap "Uninstall."
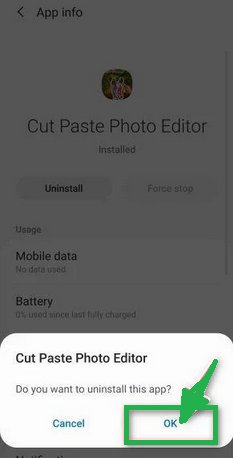
- A confirmation dialog will appear. Tap "OK" to remove the malicious app from your phone.
Step 4: Exit Safe Mode
Now that you've removed the malicious app from your phone, you can exit Safe Mode.
- Hold down the power button until you see the power off menu.
- Select the restart option. Your phone will reboot and exit Safe Mode, returning to normal operation.

By following these steps, you can effectively remove a Unwanted program virus from your Android phone and restore its security.
How to Reset Browsers
How To Reset Chrome to Default Settings
Reset Chrome for Windows
Here's a step-by-step guide to reset Google Chrome on Windows:
- Launch Google Chrome on your computer.
- Look for the three vertical dots in the top right corner of the Chrome window. Click on them to open a menu. Then, select "Settings" from this menu.
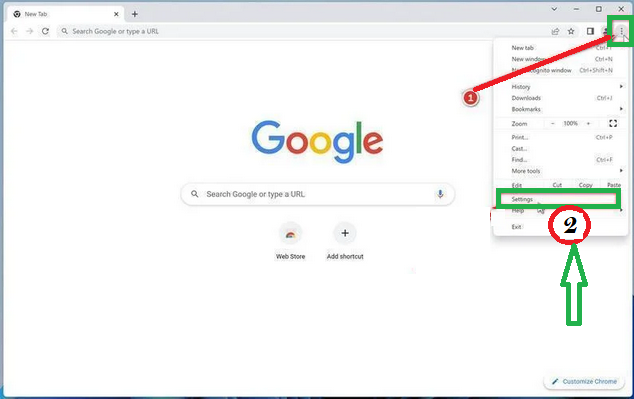
- In the Settings tab that appears, you'll see a sidebar on the left. Click on "Advanced" to get more options.
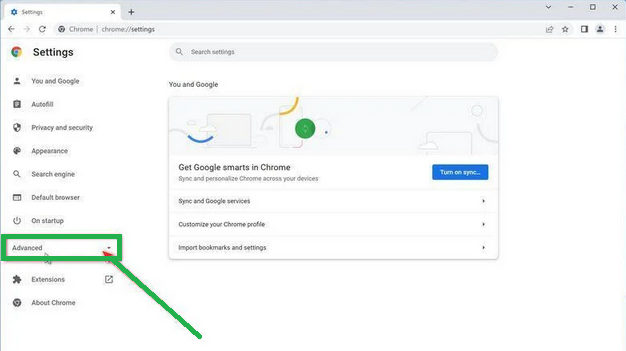
- Under the "Advanced" section in the sidebar, you'll find "Reset and clean up." Click on it.

- Now, in the main part of the window, you'll see the "Reset and clean up" section. Click on "Reset settings to their original defaults."
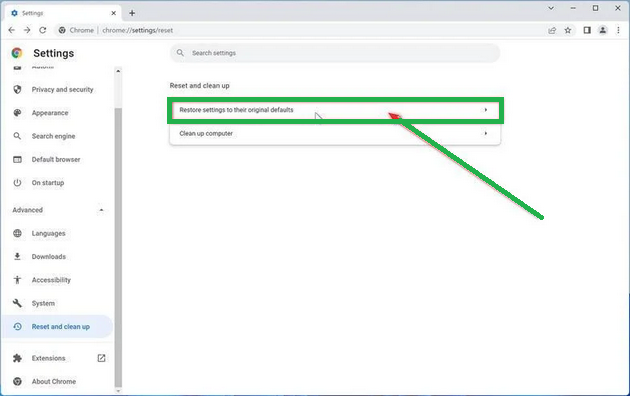
- A window will pop up to confirm the reset. It will explain what will go back to the default settings. If you're okay with that, click on "Reset settings."
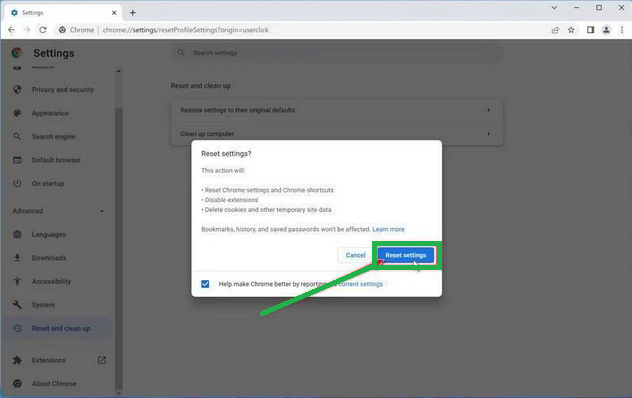
- If you find that a troublesome extension keeps coming back even after the reset, you can reset the data sync. To do this, go to chrome.google.com/sync and click on "Clear Data."

Reset Chrome for Mac
If you're using Google Chrome on a Mac and want to reset it back to its default settings, follow these steps:
- Click on the three dots in the top-right corner of Chrome (the menu button).
- Select "Settings" from the menu that appears. This will open the basic settings screen.

- In the left sidebar, click on "Reset and clean up."

- Now, click on "Reset settings to their original defaults."
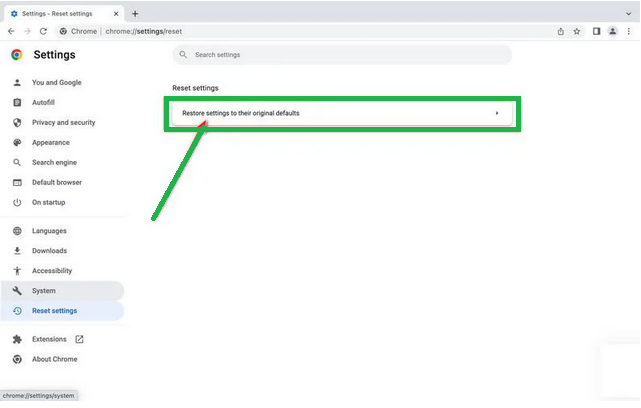
- A confirmation box will pop up, telling you what will be set back to the default settings. To complete the process, click on "Reset Settings."

Keep in mind that doing this will erase your homepage, tab settings, saved information, browsing history, and cookies. It will also disable any extensions you've installed. However, your bookmarks will be safe.
- If you're still having trouble with a malicious extension coming back even after resetting your browser, you can reset your data sync. To do this, go to chrome.google.com/sync and click on the "Clear Data" button.
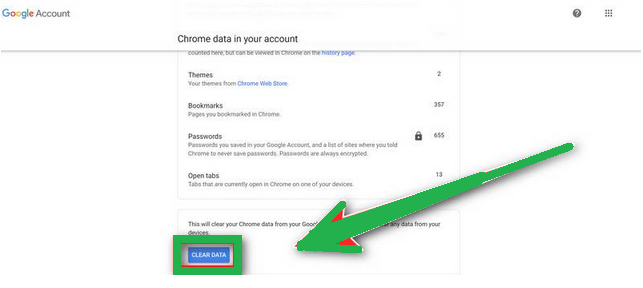
Reset Chrome for Android
Resetting Chrome to its default settings on Android isn't as straightforward as on computers, but it's doable by clearing the app data. This means getting rid of saved cookies, cache, and site settings. Here's how to do it:
- Open the "Settings" app on your Android device. You can usually find it on your home screen or in your phone's app menu.

- In the "Settings" menu, look for "Apps" or "App Manager." This will show you a list of all the apps installed on your phone.

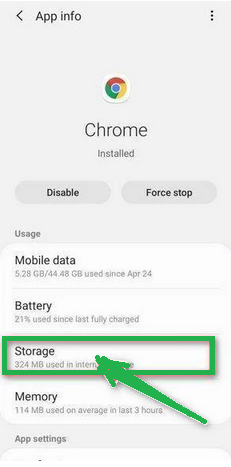
- Scroll through the list until you find the "Chrome" app, and then tap on it to view the app's details.

- Inside Chrome's app info menu, tap on "Storage."
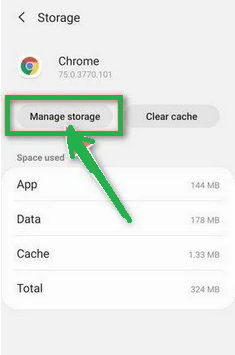
- Under the storage settings, you'll see two options – "Manage Space" and "Clear Cache." Click on "Manage Space."
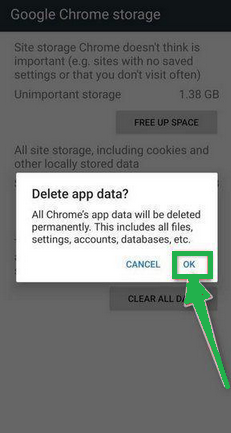
- Now, click on "Clear all Data." This will delete everything related to Chrome, including your accounts, bookmarks, and settings, essentially resetting it to its default state.

- A confirmation message will pop up, explaining what will be reset. To finish the reset process, tap "OK."
How to Reset Internet Explorer
Resetting Internet Explorer is an easy process and only takes a few minutes. Here's how you can do it:
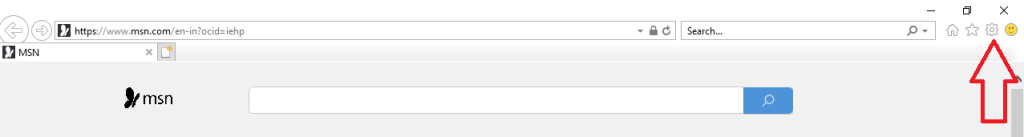
- Open Internet Explorer, which is your web browser.
- Look for a little gear icon in the top-right corner of the browser and click on it.
- Then, select "Internet Options."

- In the "Internet Options" box, click on the "Advanced" tab.
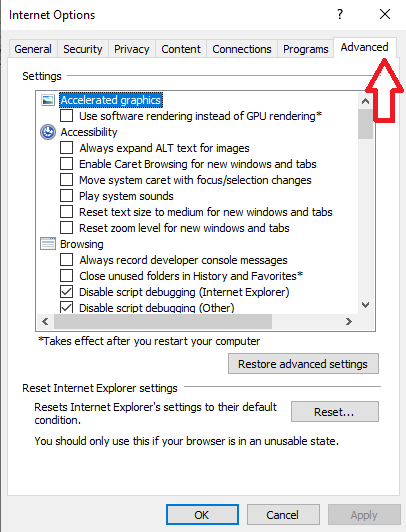
- You'll see a "Reset" button. Click on that.
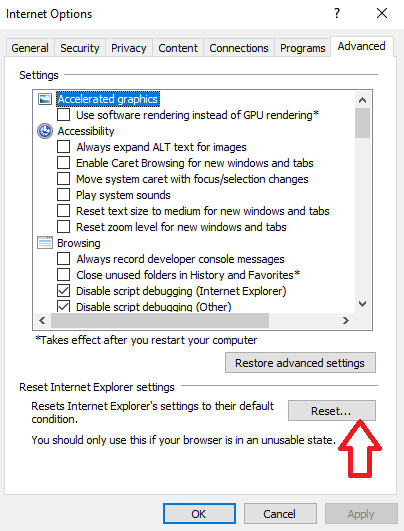
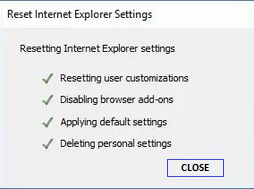
- Now, in the "Reset Internet Explorer settings" section, there's a box that says "Delete personal settings." Check this box, and then click "Reset."

- When Internet Explorer finishes the reset, a message will pop up. Click "Close" to close it. After that, close your browser, and you can open Internet Explorer again.
How To Reset Mozilla Firefox
Reset Firefox for Windows
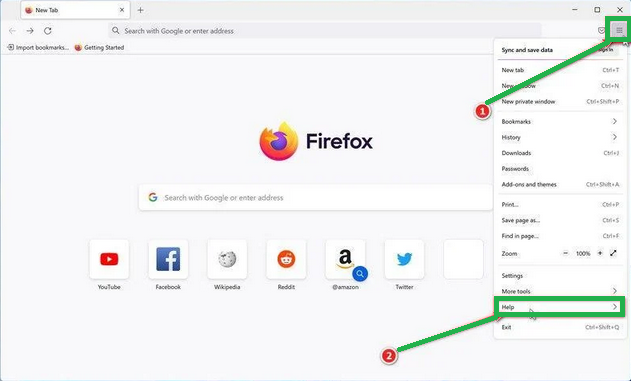
- Click on the three horizontal lines in the top right corner of Firefox to open the menu. Choose "Help" from the menu.
-
- In the "Help" menu, tap on "More troubleshooting information."

- On the "Troubleshooting Information" page, find the "Refresh Firefox" button and click it.
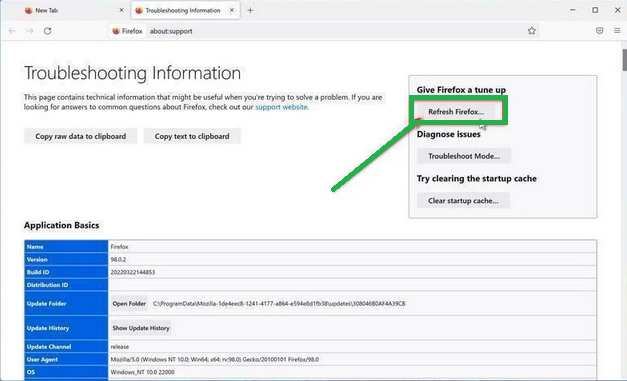
- Confirm the reset by clicking "Refresh Firefox" again in the new window that pops up.

- Firefox will close and go back to its default settings. It will show you what information it saved. Click "Finish" when it's done.
After the reset, you'll see a folder called "Old Firefox Data" on your desktop. It holds your old settings. If the reset didn't solve your problem, you can copy some of the files from this folder to the new profile that was created. But if you're sure you won't need this folder anymore, it's a good idea to delete it since it might contain sensitive information.
Reset Firefox for Mac
Resetting Firefox on a Mac is easy. Here's what you do:
- Click on the three horizontal lines in the top right corner of Firefox to open the menu. Select "Help" from the menu.

- Then, choose "Troubleshooting Information."

- On the Troubleshooting page, you'll see a "Refresh Firefox" button in the upper-right corner. Click on it.
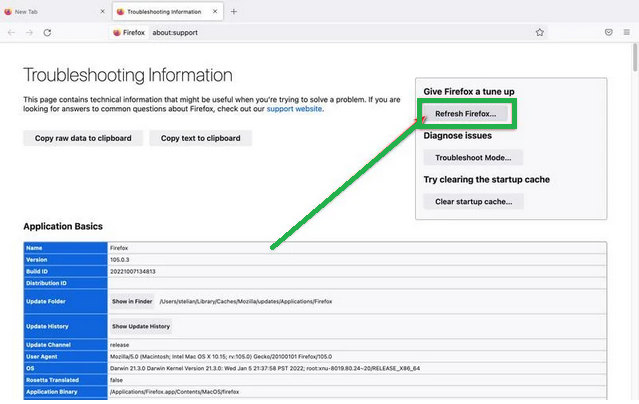
- Confirm the reset by clicking "Refresh Firefox" again in the new window.
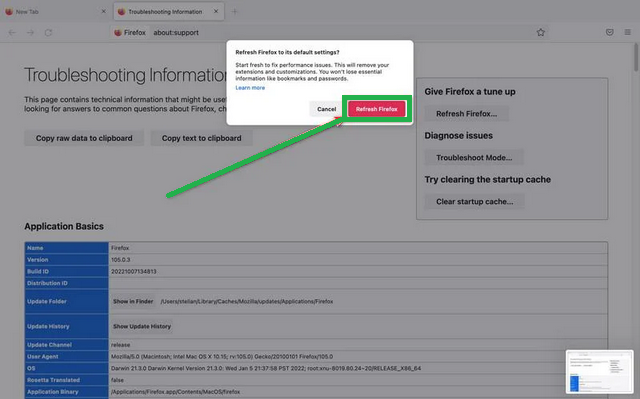
- Firefox will close and go back to its default settings. It will show you what information it saved. Click "Finish" when it's done.
That's it! Resetting Firefox on your Mac is a quick way to make it work better while keeping your important data safe.
Reset Firefox for Android
Resetting Firefox to its default settings on Android is a bit different but still doable. It involves clearing the app's data, which includes cookies, cache, and saved site settings. Here's how you can do it:
- Open your phone's "Settings" app, which you can find in your menu or on the home screen.
- In the "Settings" menu, look for "Apps" or "App Manager." This will show you all the apps installed on your phone.
- Scroll through the list of apps until you find "Firefox." Click on it to open the app's details.

- In Firefox's app menu, click on "Storage."

- In the storage settings, you'll see two options: "Manage Space" and "Clear Cache." Click on "Manage Space."

- Now, click on "Clear all data." This will delete all of Firefox's data, including your accounts, bookmarks, and settings, effectively resetting it to its default state.

- You'll see a confirmation message that explains what will be reset. To complete the reset, tap "Ok."
How To Reset Edge to Default Settings
To reset Microsoft Edge on your computer, follow these simple steps:
- Click on the three horizontal dots in the top-right corner of Microsoft Edge to open the menu. From the menu, select "Settings."

- Tap "Reset Settings" on the left side of the window.

- Now, click on "Restore settings to their default values" in the main window.
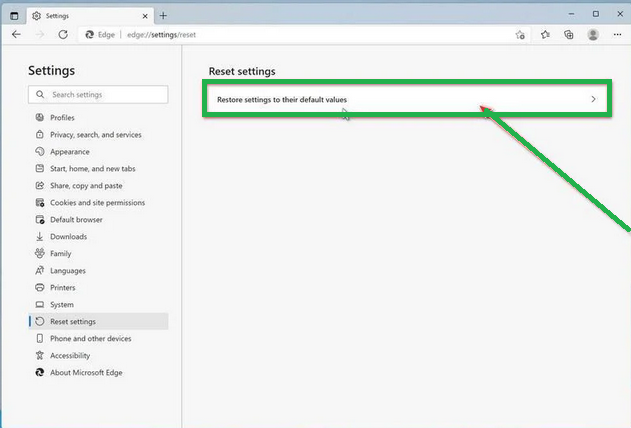
- A confirmation message will appear, explaining what will be reset. To proceed, click "Reset."
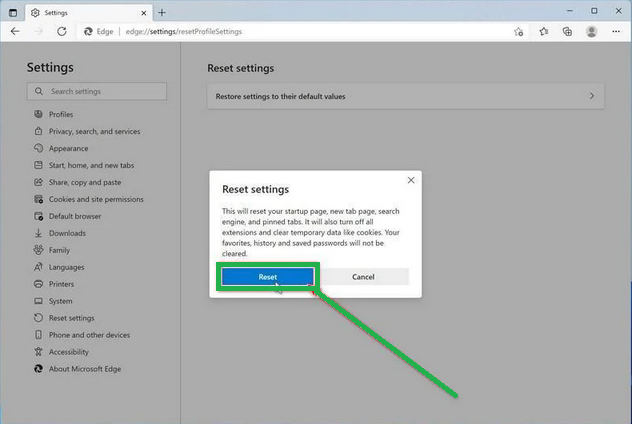
- Microsoft Edge will erase your personal data, browsing history, and disable any installed extensions. But don't worry, your bookmarks will remain safe and accessible.
How To Reset Safari
Before resetting Safari to its default settings, if you have bookmarks you want to keep, open Safari, go to the "File" menu, and choose "Export Bookmarks." Give your backup a name and save it.
To reset Safari on a Mac, you can use the Settings menu or Terminal. If you're using Safari on an iPhone or iPad, tap the iOS tab to reset the settings. This way, you won't lose your important bookmarks when you reset Safari. It's like making a copy of your bookmarks before cleaning up your browser.
Reset Safari for Mac via Settings
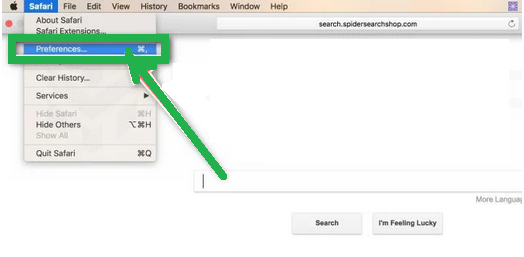
Here's how to reset Safari:
- Click "Safari" in the menu, then choose "Preferences." This opens a new window with your Safari settings.
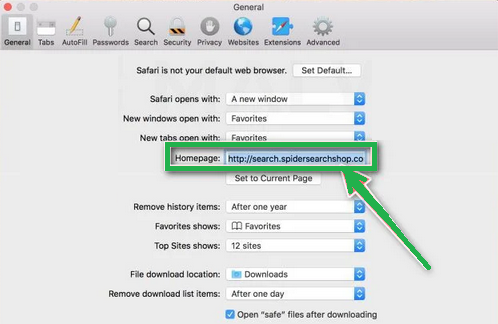
- Check your homepage in the "General" tab. If it's not what you want, change it.
- Next, click on the "Extensions" tab.

- Look for any extensions you don't remember installing or seem suspicious. It's usually safe to remove them.

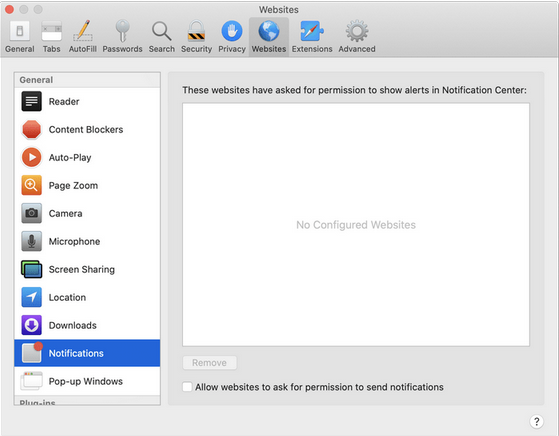
- In "Preferences," go to "Websites" and then "Notifications." Turn off the option that allows websites to ask for push notifications.
- In the Safari menu, choose "Preferences" again, then go to "Privacy." Tap on "Manage Website Data".
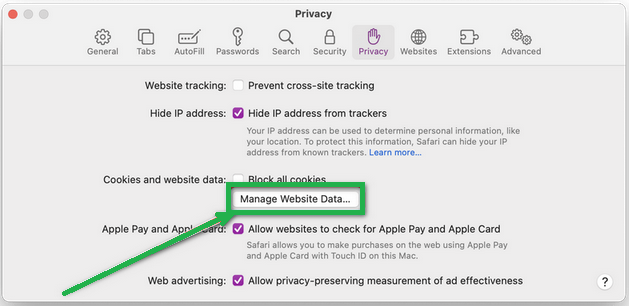
- Choose "Remove All" to clear website data.
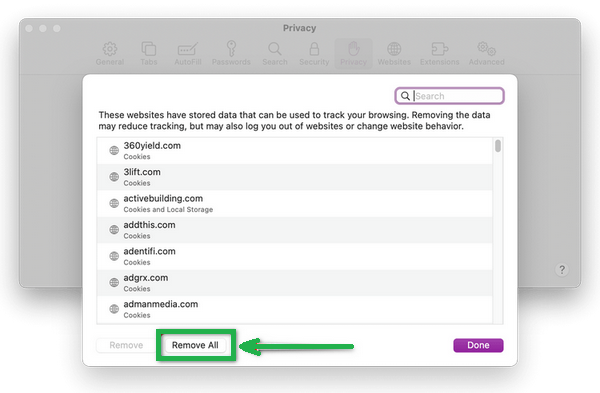
- To show the "Develop" menu, go to the "Advanced" tab in "Preferences" and enable "Show Develop menu in menu bar."
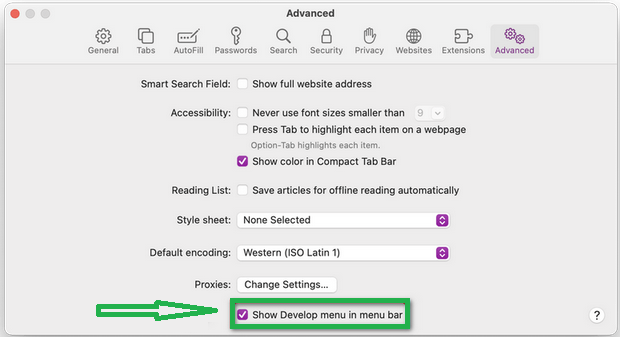
- Click on "Develop" in the menu bar, and then select "Empty Caches" to clear out temporary files.
Reset Safari for Mac via Terminal
To reset Safari on your Mac, follow these steps:
- Open the "Terminal" app (you can search for it using Spotlight with "Cmd + Space").
- Go to the Apple menu at the top-left and choose "Force Quit." Select "Safari" to close it completely.
- Enter the commands one by one in Terminal. It will ask for confirmation to delete files. Type "y" and press "Enter" after each command.
mv ~/Library/Safari ~/Desktop/Safari-`date +%Y%m%d%H%M%S`;
rm -Rf ~/Library/Cache/*;
rm -Rf ~/Library/Caches/Apple\ -\ Safari\ -\ Safari\ Extensions\ Gallery;
rm -Rf ~/Library/Caches/Metadata/Safari;
rm -Rf ~/Library/Caches/com.apple.Safari;
rm -Rf ~/Library/Caches/com.apple.WebKit.PluginProcess;
rm -Rf ~/Library/Cookies/*;
rm -Rf ~/Library/Cookies/Cookies.binarycookies;
rm -Rf ~/Library/Preferences/Apple\ -\ Safari\ -\ Safari\ Extensions\ Gallery;
rm -Rf ~/Library/Preferences/com.apple.Safari.LSSharedFileList.plist;
rm -Rf ~/Library/Preferences/com.apple.Safari.RSS.plist;
rm -Rf ~/Library/Preferences/com.apple.Safari.plist;
rm -Rf ~/Library/Preferences/com.apple.WebFoundation.plist;
rm -Rf ~/Library/Preferences/com.apple.WebKit.PluginHost.plist;
rm -Rf ~/Library/Preferences/com.apple.WebKit.PluginProcess.plist;
rm -Rf ~/Library/PubSub/Database;
rm -Rf ~/Library/Safari/*;
rm -Rf ~/Library/Safari/Bookmarks.plist;
rm -Rf ~/Library/Saved\ Application\ State/com.apple.Safari.savedState;
Reset Safari for iOS (iPhone or iPad)
To reset Safari on your iPhone or iPad, follow these steps:
- Open the "Settings" app.

- Turn on "Airplane Mode" to disconnect from the internet temporarily and block unwanted access.
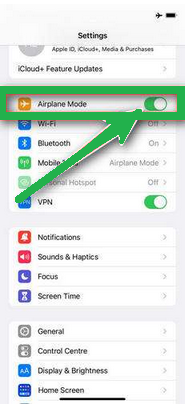
- Scroll down and click on "Safari."
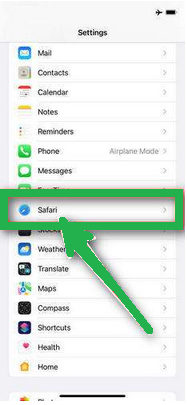
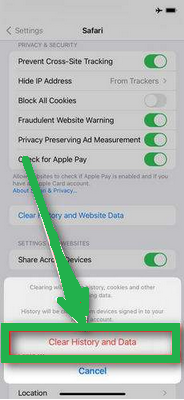
- Now, choose "Clear History and Website Data."

- Confirm by tapping "Clear History and Data" in the pop-up window.
- While in Safari settings, make sure to turn on "Block Pop-ups" and "Fraudulent Website Warning."
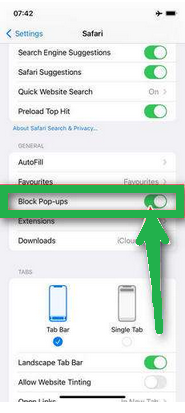
These steps clear your browsing history, website data, and other information stored by websites you visited. Also, by enabling "Block Pop-ups" and "Fraudulent Website Warning," you can enhance your browsing experience and protect yourself from unwanted ads and potentially harmful websites.
Recommended Security Software (SpyHunter)
SpyHunter acts like a guardian for your computer, shielding it from nasty stuff like malware and spyware. Using smart scanning, it hunts down and kicks out harmful programs sneaking around your system. It’s not just a detective; it also stops new threats from barging in. Anyone, whether tech-savvy or not, can easily use it because of its simple design. Plus, it keeps learning and gets regular updates to stay ahead of the bad guys. If you want a solid defender for your PC against digital troublemakers, SpyHunter is a reliable choice, always ready to keep your computer safe.
Step 1: Download SpyHunter 5 for your device through the provided link. Obtain it by clicking below.
Step 2: Proceed to the location where the installer is saved in your system. Typically, the file is stored in the “Downloads” directory. Execute the setup process by double-clicking on the installer file.
Step 3: Choose your desired language and press the “OK” button. This action triggers the installer initialization. When prompted, click the “Continue” button to proceed with the installation process.

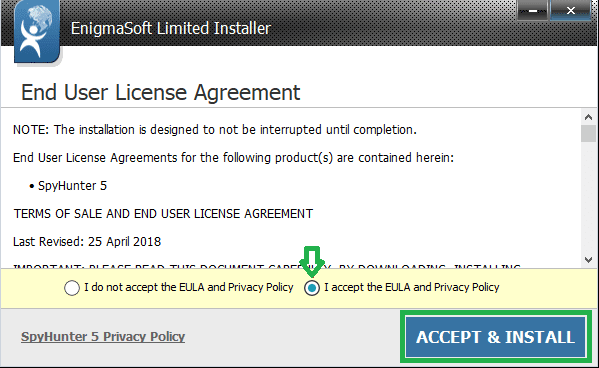
Step 4: During installation, you’ll encounter a prompt to approve the ‘EULA and Privacy Policy.’ Opt for ‘I accept the EULA and Privacy Policy’ and then select the ‘Accept & Install’ button. This step is necessary to proceed with the installation process of the application.
Step 5: Initiate the installation process, and observe the progression through the visible progress bar. The process may require some time for completion. Once finished, a notification confirming successful installation will be displayed.

Step 6: Upon installation completion, SpyHunter will automatically launch. The following screen will be displayed for your attention.

Step 7: Additionally, the scanner will initiate a comprehensive scan of your computer to identify potential threats within your device. Throughout the scan, it will present you with information such as the detected threat’s name, security level, and specific details about the threat. Relax and wait for the scan process to conclude.
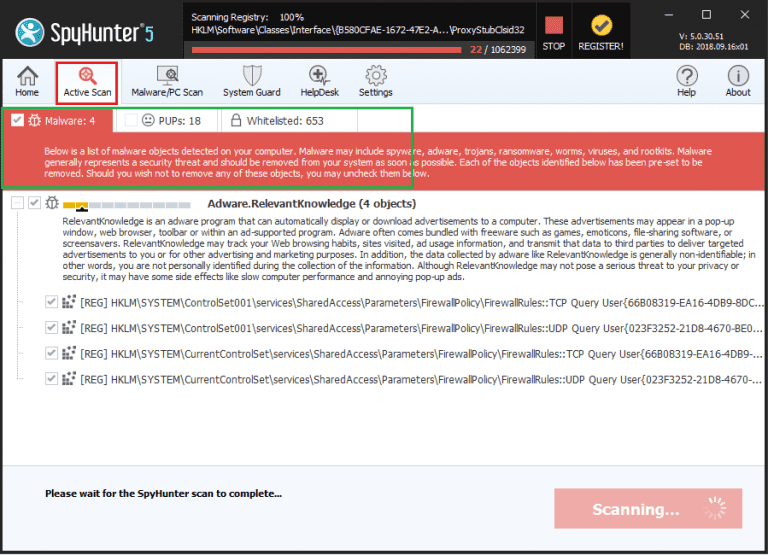
Step 8: Upon completion of the scan, press the “Next” button to continue the process.
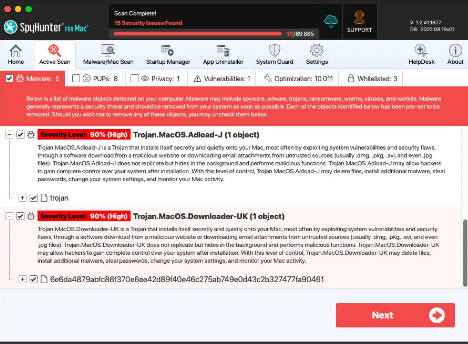
Step 9: To finalize the removal process, the application will prompt you to purchase its licensed version. Alternatively, you have the option to opt for a 7-day free trial, during which the software will be fully operational, allowing you to eliminate all identified threats.
Special Offer
In order to remove Aviationshop.com hassle free, we suggest you to scan the PC with powerful SpyHunter antimalware scanner. The fully functional free Trial of SpyHunter is Available for 7 days (Windows Version) with Credit Card required. There are no upfront charges within this period. Further, no charge will apply if you cancel 2 business days before the trail ends. For Mac Users, it is suggested to use Combo Cleaner which is a powerful antivirus and System optimizer.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.