How to Remove Trojan Virus from Computer

Details About Trojan Horse
A Trojan Horse, or just “Trojan” for short, is a sneaky kind of malicious software. It pretends to be something harmless, like a game or an app, but once it gets into your computer, it can do bad things. Imagine it’s like a secret spy that tricks its way in.
Once it’s inside, it can act like a regular user of your PC. It can mess with your files, change stuff, or even delete things. It’s pretty clever because it doesn’t spread by itself like a virus or worm. Instead, it needs someone to willingly download and run it, often without realizing it’s harmful.
People who create Trojans use various tricks, like pretending to be a trustworthy email or a legitimate-looking website. They might also use sneaky tactics to make you click on things, like pretending to be a software update or a fun game. Once you’ve got a Trojan, it can do nasty things, like stealing your personal information or messing up your computer.
Sometimes, these crooks even demand money from you to undo the damage they’ve caused. Or they might sell your stolen info to other bad actors on the internet.
So, the bottom line is to be really careful about what you download and click on, especially if it’s from an unknown source. Trojans are like digital spies that pretend to be friendly but can cause a lot of trouble once they’re inside your work-station.
Types of Trojan and their Aim

Trojans are a common type of sneaky computer malware used by cybercriminals for various purposes. Imagine them like digital spies or tricksters that pretend to be something they’re not. Here are 10 types of Trojans and what they do:
- Backdoor Trojan: This Trojan lets a cybercriminal set up secret entry points into a computer or network. It’s like leaving the back door open for them.
- Banking Trojan: This one targets your money. It’s designed to steal your banking info, credit card numbers, or any other financial details you use online.
- Exploit Trojan: Exploit Trojans are like lockpick experts. They find weaknesses in your computer software and use them to break in.
- SMS Trojan: This Trojan mainly affects mobile devices. It can read and send text messages without you knowing. Some even send expensive texts to premium numbers, making the cybercriminals money.
- Trojan Game Thief: Gamers beware! This Trojan goes after your gaming accounts, trying to steal your login info.
- Rootkit Trojan: This Trojan hides deep within your computer, making it hard to find. It’s like a secret agent that doesn’t want to be caught.
- DDoS Attack Trojan: Some Trojans team up with others to create a ‘zombie network.’ This network can then overwhelm websites and networks with too much traffic, causing them to crash. It’s like a bunch of digital zombies attacking at once.
- Downloader Trojan: This one’s like a delivery person with a hidden agenda. It brings other malware onto your device, making it even more vulnerable.
- Fake AV Trojan: This Trojan pretends to be antivirus software. It warns you of threats on your computer, but it’s lying. It’s actually ransomware that asks you to pay to remove the fake threats.
- Ransom Trojan: Just like regular ransomware, this Trojan locks up your computer or files. To get them back, you have to pay a ransom.
Risks Caused by Trojan Virus

Trojan viruses are malicious software that can bring various risks and threats to your computer and personal data. First and foremost, they have the potential to steal sensitive information, such as login credentials, credit card details, and personal documents. This stolen data can be exploited for financial gain, leading to identity theft or fraudulent transactions.
Financial loss is another significant risk associated with Trojans, particularly banking Trojans. These malicious programs can access your online banking accounts, making unauthorized transfers and withdrawals, resulting in monetary losses that can be challenging to recover. Trojans can also inflict damage on your device. Some are designed to corrupt or delete files, rendering your PC unusable. Others can disrupt system functionality, causing frequent crashes and overall slowdowns in performance.
Privacy invasion is a grave concern with Trojans, as they can grant cybercriminals unauthorized access to your computer. This access allows them to monitor your online activities, capture screenshots, or even activate your webcam without your consent. Ransomware is another threat linked to Trojans. Some Trojans carry ransomware payloads, encrypting your files and demanding a ransom for their release. Paying the ransom is risky and doesn’t guarantee the safe return of your files.
Furthermore, Trojans can turn your PC into a part of a botnet, a network of infected devices used for malicious purposes, such as launching large-scale cyberattacks like Distributed Denial of Service (DDoS) attacks. They can also act as gateways for other types of malware, enabling more dangerous viruses to infiltrate your system. Finally, some Trojans, known as backdoors, can allow attackers to gain remote control of your computer, opening the door to various forms of misuse.
Common Symptoms of Trojan Attack

Common Trojan attack symptoms include computer slowdown, unusual network activity, and unauthorized access or changes on your PC, indicating potential malware infection. Let’s discuss about them in detail:
- Slowdown: A noticeable slowdown in your computer’s performance is a common symptom of a Trojan attack. Trojans often consume a significant amount of your computer’s processing power and memory. This can cause your device to become sluggish, with programs taking longer to open, files to save, and web pages to load. You may also experience delays in basic tasks like typing or moving your mouse cursor. If you suddenly observe a significant drop in your computer’s speed and responsiveness, it could be a sign of a Trojan infection.
- Unusual Activities on the Network: Trojans can generate unusual network activities. You might notice an increase in data usage or network traffic even when you’re not actively using the internet. Trojans often communicate with remote servers controlled by cybercriminals, sending stolen data or receiving commands. If your network monitoring tools or firewall alerts you to unusual outbound traffic or connections to suspicious IP addresses, it could indicate a Trojan infection.
- Unidentified Access on PC: Trojans can grant unauthorized access to your computer. You may notice strange or unexpected activities on your PC, such as files mysteriously appearing, disappearing, or being modified without your consent. Unauthorized changes to system settings, the installation of new programs, or unfamiliar icons on your desktop are also warning signs. If you see evidence of someone or something accessing and controlling your computer without your knowledge or permission, it’s a clear indication of a potential Trojan infection.
How to Remove Trojan horse from Windows 11
To get rid of a Trojan on your Windows computer, follow these straightforward steps:
- Open your computer’s settings by pressing “Windows + I” or right-clicking the “Start” button and choosing “Settings.”

- In the settings window, click on “Apps” and then select “Apps & Features.”

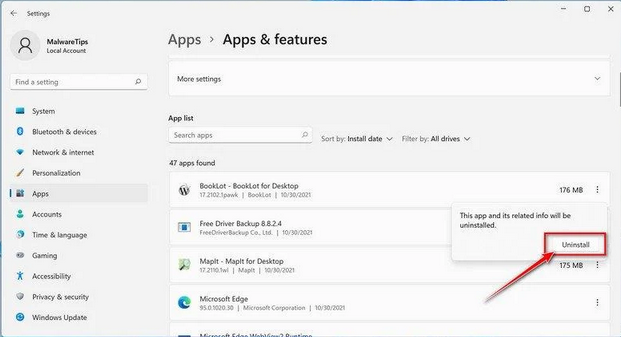
- You’ll see a list of installed programs. Scroll through them and look for anything suspicious or unfamiliar. To make it easier, you can sort the list by the installation date. Just click “Sort by” and pick “Install date.”
- Keep an eye out for any programs that don’t seem right – things you don’t remember installing or that don’t sound like legitimate software. When you find a suspicious program, click the three dots next to it and choose “Uninstall.”

- A message box will pop up. Confirm the uninstall process by clicking “Uninstall” and follow any prompts that come up to complete the removal.
- It’s crucial to read all the prompts carefully because some malicious programs might try to sneak in extra things, hoping you won’t notice.
- Once you’ve successfully removed the malicious programs from your computer, you’ve taken a big step in getting rid of the Trojan.
How to Remove Trojan Virus from Windows 10
To remove a Trojan from a Windows 10 computer, follow these steps:
- Open the “Settings” app by press the “Windows key + I” on your keyboard. Alternatively, you can click the “Start” button on the taskbar and then choose “Settings” (the gear icon).

- In the “Windows Settings” window, you’ll see various options. Click on “Apps.” By default, it should take you to “Apps and Features,” but if not, select it from the options on the left.

- In the “Apps & Features” settings, scroll through the list of installed programs. Look for anything that seems unfamiliar or suspicious. To help with this, you can sort the programs by their installation date. To do this, click “Sort by” and pick “Install date.”
- Keep an eye out for any program that you don’t remember downloading or that doesn’t seem like a legitimate piece of software. When you find a suspicious program, click on it and then choose “Uninstall” from the menu that appears.
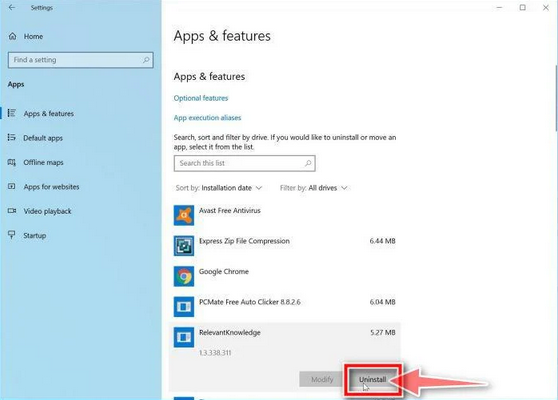
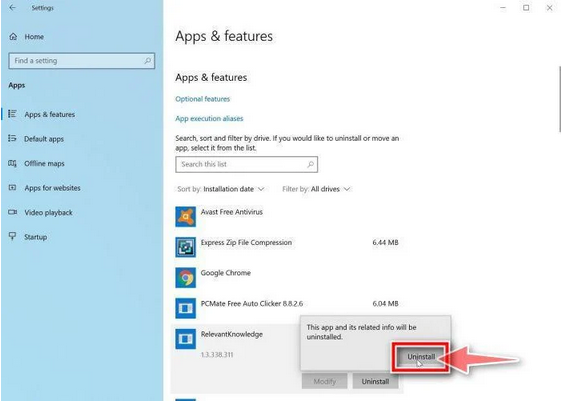
- A message box will pop up to confirm the uninstallation process. Click “Uninstall” to confirm and follow any additional prompts that come up to complete the removal.
- It’s essential to carefully read all the prompts because some malicious programs might try to sneak in additional things during the process, hoping you won’t notice.
- Once you’ve gone through these steps successfully, the malicious program will be removed from your computer.
How to Remove Trojan Virus from Windows 7
To remove a Trojan from Windows 7, follow these steps:
- Click the “Start” button and select “Control Panel.”
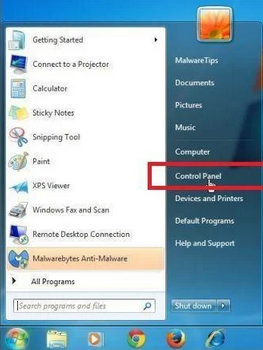
- In the Control Panel, click “Uninstall a Program” under the “Programs” category.

- You’ll see a list of all installed programs in the “Programs and Features” screen. Find any suspicious or unfamiliar programs, click to highlight them, and then click “Uninstall.”
- Look for anything that doesn’t seem legitimate or you don’t remember installing.

- Confirm the uninstallation in the message box by clicking “Yes” and follow any prompts to complete the removal. Read carefully, as some malicious programs try to slip in unnoticed.
- Once you’ve completed these steps, the malicious software will be removed from your computer.
How to Remove Trojan Virus from Android/Mobile
To remove a Trojan virus from your Android phone, follow these simple steps:
Step 1: Start in Safe Mode
First, we’ll start your phone in Safe Mode. Safe Mode boots your Android with only the essential apps and settings, preventing malicious apps from interfering.
- Long-press your phone’s power button (usually found on the side of your phone) until the power off menu appears.
- When the menu appears, tap and hold the “Power off” button on your screen. You’ll see a “Safe mode” option.
- Tap on “Safe mode” to enter it.

- Your phone will restart in Safe Mode, and you’ll see the “Safe Mode” text at the bottom left corner of your device.

If you can’t find Safe Mode on your phone, you can activate Airplane mode instead to cut off network connections.
Step 2: Check for Malicious Apps with Administrator Privileges
In this step, we’ll check if there are any malicious apps with administrator privileges on your phone. These privileges are sometimes used for legitimate purposes but can also be exploited by malicious apps to prevent their removal.
- Tap the “Settings” app on your phone’s menu or home screen.
- In the “Settings” menu, look for “Biometrics and Security” (or similar) and then navigate to “Other Security Settings” and “Device admin apps.” The location of this option may vary depending on your Android version or phone brand.
If you can’t find “Device admin apps” easily, you can use your phone’s search function to look for it.
- Once you’re in the list of device admin apps, disable admin rights by tapping the option next to the app. This will remove the checkmark or turn off the toggle button. Some phones also let you tap the app in the admin apps list and then use the “Uninstall” link to remove it immediately.

Step 3: Check for Malicious Apps
While your phone is still in Safe Mode, we’ll check for malicious apps.
- Tap the “Settings” app.

- In the “Settings” menu, tap on “Apps” or “App Manager” to view all installed applications on your phone.

- You’ll see a list of all installed apps. Scroll through the list and look for any suspicious apps that you don’t remember downloading or that don’t seem genuine. Malware is often hidden in apps like photo editors, weather apps, or camera apps.
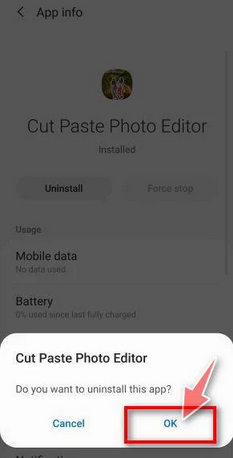
- When you find a suspicious app, tap on it to uninstall. This won’t open the app but will take you to the app details screen. If the app is currently running, tap “Force stop,” then tap “Uninstall.”

- A confirmation dialog will appear. Tap “OK” to remove the malicious app from your phone.
Step 4: Exit Safe Mode
Now that you’ve removed the malicious app from your phone, you can exit Safe Mode.
- Hold down the power button until you see the power off menu.
- Select the restart option. Your phone will reboot and exit Safe Mode, returning to normal operation.

By following these steps, you can effectively remove a Trojan virus from your Android phone and restore its security.
In conclusion, Trojan viruses are deceptive malware with various types, causing significant risks such as data theft, system damage, and financial loss. Common symptoms include system slowdown and network irregularities. Removing Trojans involves identifying and uninstalling malicious apps. On Windows, for Windows 10, utilize the Settings app, while Windows 7 users can access the Control Panel. Android users should boot into Safe Mode to remove malicious apps. Staying vigilant, practicing safe browsing habits, and regularly updating antivirus software are key to mitigating Trojan threats across different platforms.