Is VolfDex.com a Scam? Beware and Investigate!

About VolfDex.com Bitcoin Promo Code Scam
Have you heard of VolfDex.com? It’s a website that promises to give you free Bitcoin, but it’s actually a big scam. Here’s how it works.
Scammers use fake videos of famous people like Cristiano Ronaldo, Elon Musk, Bill Gates, Mark Zuckerberg, and Drake to trick people. In these videos, they say that if you sign up on VolfDex.com and enter a special code, you’ll get free Bitcoin. Sounds great, right? But it’s not.
When you sign up and enter the code, you do see some Bitcoin in your account. But here’s the catch: you can’t take it out unless you deposit some of your own Bitcoin first. They say it’s to “activate” your account, but really, it’s just a way for them to steal your money.
So, if you fall for it and send them your Bitcoin, they take it and disappear. You’re left with nothing. And the worst part is, those celebrities had nothing to do with it. They’re just being used to make the scam seem more legit.
It’s a sneaky trick, preying on people’s trust in famous names and their desire to get rich quick. But don’t be fooled. VolfDex.com is not a real trading platform, and there are no free Bitcoin giveaways. It’s all just a ploy to steal your hard-earned money.
So, if you see those videos or ads popping up on social media, don’t fall for it. Don’t give them any of your Bitcoin, and warn your friends too. The only people getting rich off this scam are the ones behind it. Stay safe and stick to reputable sources when it comes to cryptocurrency.
Modus Operandi of VolfDex.com Scam

Let’s break down how this deceitful plot unfolds at each stage.
Firstly, VolfDex.com aims to attract potential victims to their website using various methods. They run ads on popular social media platforms like Facebook, Instagram, and TikTok. These ads, often created with fake user accounts, boast about incredible profits through crypto trading and investing. Scammers also directly reach out to individuals active in cryptocurrency spaces on social media and messaging apps, posing as successful crypto traders and offering assistance in investing with VolfDex.com. Additionally, existing victims are encouraged to refer friends and family in exchange for small bonuses. Sometimes, scammers may even use the “pig butchering” scam to build relationships before introducing VolfDex.com as an investment opportunity. The ultimate goal of these tactics is to drive targets to the VolfDex.com website and convince them to sign up for an account.
Once users land on the VolfDex.com site, they are presented with impressive-looking statistical charts and records that indicate massive profits from trades. These fabricated metrics include unrealistic percentage gains, rapid balance growth, a flawless transaction history with minimal losses, and leaderboards showcasing accounts with extraordinary gains over short periods. However, it’s essential to understand that all of these metrics are entirely fake. There are no real trades happening, and any account growth displayed is purely imaginary. The intention is to persuade targets that they can make substantial profits by depositing more cryptocurrency or cash.
After reviewing these misleading metrics, users are prompted to make an initial deposit to start trading and investing. Deposits must be made in cryptocurrency like Bitcoin, Ethereum, or stablecoins. Following a deposit, the account page reflects the balance growth according to the fake statistics. Users are then encouraged to deposit more, with promises of taking advantage of market conditions or unlocking premium features.
However, when a user attempts to withdraw any amount, they face obstacles and excuses. They might be told they need to provide personal ID for verification, that withdrawals are delayed due to high volume, that they must deposit more to meet a minimum withdrawal limit, or that the account is temporarily locked for security purposes. In reality, withdrawals are permanently disabled because the scammers’ objective is to steal deposits, not facilitate withdrawals.
If users catch on to the scam and start demanding withdrawals or threatening authorities, VolfDex.com simply disappears. The website goes down, social media accounts are deleted, and the scammers vanish. They may even resort to threatening users for reporting them, falsely claiming the user engaged in illegal trading to deter reporting.
Once the scam is exposed, the scammers take their stolen cryptocurrency, erase their tracks, and reappear under a new name to repeat the process. Unfortunately, users seldom recover their money unless authorities can trace it. In essence, the VolfDex.com scam preys on people’s desire for financial gain, using deceptive tactics and fabricated success stories to exploit their trust and steal their hard-earned funds.
How to Identify VolfDex.com Scam and Avoid it:

Watch out for signs that could indicate the VolfDex.com scam, despite its efforts to appear legitimate. If the team behind VolfDex.com remains anonymous, it’s a red flag; legitimate companies showcase their team members. Be wary of high-pressure tactics, where scammers insist on quick and frequent deposits for massive profits—legitimate investors don’t push like this. Unrealistic returns in the hundreds or thousands of percent over short periods are clear warning signs. If pitches seem too smooth and scammers have perfect answers to every question, be cautious.
Check for portfolio transparency; if VolfDex.com obscures what trades are happening and what assets you supposedly own, it’s suspicious. The registration of VolfDex.com’s website in the past few months indicates a lack of a long-term track record. If there’s no transparency about who runs VolfDex.com and how trading results are achieved, it suggests deception. The most significant red flag is the inability to withdraw funds—if you can deposit but not withdraw, your funds may be lost.
Protect yourself by recognizing these warning signs early and avoiding involvement with VolfDex.com scammers. Be cautious, ask questions, and seek transparency to ensure the legitimacy of any investment opportunity.
Social Media Platforms are Used to Promote VolfDex.com

Cryptocurrency scammers often exploit social media platforms and direct messaging apps to manipulate potential victims. Here are some simple tips to identify and avoid scams through these channels.
- Beware of Unsolicited Messages: Be cautious of direct messages on platforms like WhatsApp, Instagram, or Telegram promoting cryptocurrency investments. Unsolicited messages about investment opportunities are usually scams. Instead of responding, report and block the account to protect yourself.
- Never Share Personal Information: Avoid giving out personal information such as your ID, bank details, or cryptocurrency wallet information based solely on social media or messaging app messages. If you cannot independently verify the legitimacy of a “salesperson,” consider it a potential attempt at identity theft or financial fraud.
- Approach Social Media Platforms Skeptically: Scammers play on the fear of missing out (FOMO) and present their platforms as exclusive opportunities for wealth. Be wary of accounts or ads guaranteeing returns, pressuring quick action, or promising secret money-making methods. Question why they would share such a strategy with random users rather than keeping the profits for themselves.
- Check Site Registrations and Domains: If you receive a link, investigate when the site was registered and its domain history. Scam sites often use newly registered domains and disposable hosting. Search for brand names along with keywords like “scam” or “review” to find potential warnings.
- Seek Verified Checkmarks and Reputation Indicators: Legitimate companies can often verify their accounts on platforms like Facebook and Instagram. Lack of official checkmarks should raise skepticism. Additionally, genuine companies provide contact information, business registrations, and client reviews readily.
- Research Profiles Spreading Investment Offers: Scam accounts often use stolen or AI-generated profile photos and have minimal posts unrelated to their investment promotions. Compare them against legitimate brands that you recognize – legitimate companies will have a long history of varied organic posts building their brand.
Stay alert on social media! Easy cryptocurrency gains often lure scams. Be cautious—research and stay vigilant. If any online investment opportunity seems fishy, step back, and investigate. Don’t let FOMO trick you into scams. With knowledge, scammers can’t exploit you. Protect yourself online by staying informed and being careful with tempting offers.
Things to do if You become a Victim of VolfDex.com

If you’ve fallen victim to the VolfDex.com scam, don’t blame yourself; these scammers are skilled manipulators. Take these steps immediately to address the situation and potentially recover your losses.
- Alert your bank and crypto exchanges: Contact your bank and any cryptocurrency exchanges you use. Inform them about the scam, indicating potential fraudulent activity. This action may help prevent further losses by freezing your accounts.
- Report the Scam: File reports about your experience on platforms such as BBB Scam Tracker, FTC Complaint Assistant, and with regional law enforcement agencies that accept online fraud reports. Reporting increases the chances of investigation and legal action. Provide any evidence you documented during the scam.
- Consult with lawyers: Consult with an attorney specializing in cybercrime, investment fraud, and cryptocurrency to understand your options for recovering losses. Legal counsel can guide you on whether civil action or joining a class-action suit is appropriate.
- Record details: Gather evidence from the beginning to the end of the scam. Save ads, social media conversations, screenshots, transaction records, usernames, and contact information related to VolfDex.com. This evidence is crucial for recovery efforts.
- Cease all interaction and actions: Cease all communication with anyone associated with VolfDex.com and immediately halt any further activity on the platform. Refrain from providing additional information or paying supposed “fees” to withdraw funds. Engaging further with scammers won’t improve the situation.
- Stay vigilant for recovery efforts: Be cautious of potential recovery scams where scammers pose as investigators or lawyers claiming they can recover your money for an upfront fee. Stay wary of guarantees and requests for payment in these situations.
- Keep a close watch: Keep a close eye on your bank accounts, credit cards, and crypto exchange accounts used for transactions with VolfDex.com. Look for unauthorized transactions and report them promptly. If possible, freeze your accounts for added security.
- Alert your connections: Inform your family, friends, and social media connections about the scam to prevent more victims. Share details and warning signs to help others protect themselves from falling into similar traps.
While the VolfDex.com scam is sophisticated, taking swift action after discovering the fraud is crucial. By following these steps, victims can protect themselves, potentially recover their losses, and contribute to efforts to investigate and shut down scams. Remember, seeking help and reporting the incident is a crucial part of the recovery process.
Special Offer
In order to remove VolfDex.com hassle free, we suggest you to scan the PC with powerful SpyHunter antimalware scanner. The fully functional free Trial of SpyHunter is Available for 7 days (Windows Version) with Credit Card required. There are no upfront charges within this period. Further, no charge will apply if you cancel 2 business days before the trail ends. For Mac Users, it is suggested to use Combo Cleaner which is a powerful antivirus and System optimizer.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
How to remove unwanted program from Windows 11
To get rid of an unsafe program on your Windows computer, follow these straightforward steps:
- Open your computer's settings by pressing "Windows + I" or right-clicking the "Start" button and choosing "Settings."

- In the settings window, click on "Apps" and then select "Apps & Features."
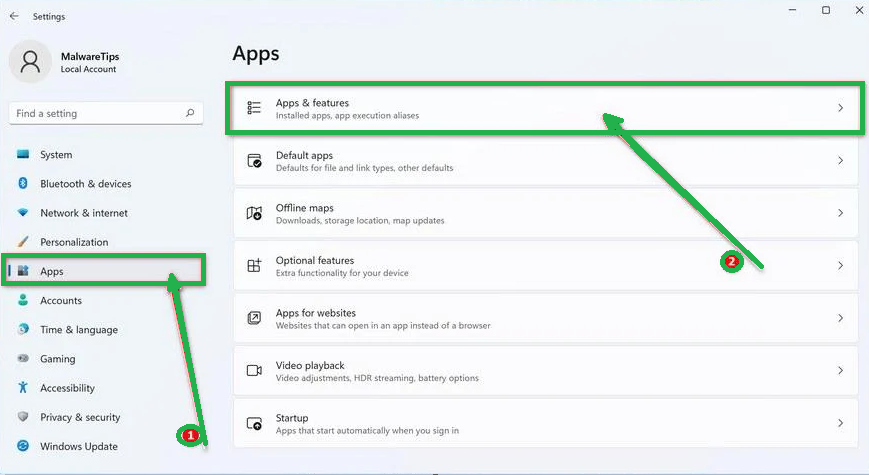
- You'll see a list of installed programs. Scroll through them and look for anything suspicious or unfamiliar. To make it easier, you can sort the list by the installation date. Just click "Sort by" and pick "Install date."
- Keep an eye out for any programs that don't seem right – things you don't remember installing or that don't sound like legitimate software. When you find a suspicious program, click the three dots next to it and choose "Uninstall."

- A message box will pop up. Confirm the uninstall process by clicking "Uninstall" and follow any prompts that come up to complete the removal.
- It's crucial to read all the prompts carefully because some malicious programs might try to sneak in extra things, hoping you won't notice.

- Once you've successfully removed the malicious programs from your computer, you've taken a big step in getting rid of the unwanted program.
How to Remove Unwanted program Virus from Windows 10
To remove an unwanted program from a Windows 10 computer, follow these steps:
- Open the "Settings" app by press the "Windows key + I" on your keyboard. Alternatively, you can click the "Start" button on the taskbar and then choose "Settings" (the gear icon).
- In the "Windows Settings" window, you'll see various options. Click on "Apps." By default, it should take you to "Apps and Features," but if not, select it from the options on the left.
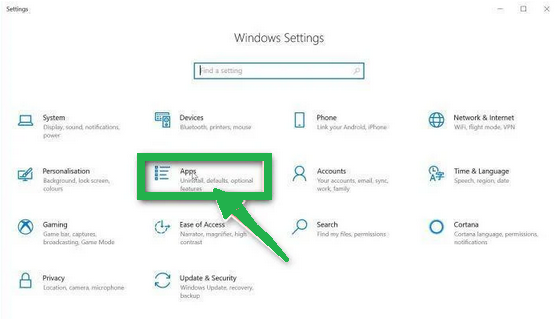
- In the "Apps & Features" settings, scroll through the list of installed programs. Look for anything that seems unfamiliar or suspicious. To help with this, you can sort the programs by their installation date. To do this, click "Sort by" and pick "Install date."
- Keep an eye out for any program that you don't remember downloading or that doesn't seem like a legitimate piece of software. When you find a suspicious program, click on it and then choose "Uninstall" from the menu that appears.

- A message box will pop up to confirm the uninstallation process. Click "Uninstall" to confirm and follow any additional prompts that come up to complete the removal.
- It's essential to carefully read all the prompts because some malicious programs might try to sneak in additional things during the process, hoping you won't notice.

- Once you've gone through these steps successfully, the malicious program will be removed from your computer.
How to Remove Unwanted program Virus from Windows 7
To remove an unwanted program from Windows 7, follow these steps:
- Click the "Start" button and select "Control Panel."
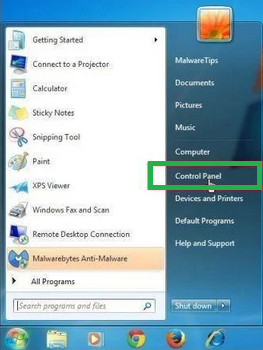
- In the Control Panel, click "Uninstall a Program" under the "Programs" category.

- You'll see a list of all installed programs in the "Programs and Features" screen. Find any suspicious or unfamiliar programs, click to highlight them, and then click "Uninstall."
- Look for anything that doesn't seem legitimate or you don't remember installing.

- Confirm the uninstallation in the message box by clicking "Yes" and follow any prompts to complete the removal. Read carefully, as some malicious programs try to slip in unnoticed.
- Once you've completed these steps, the malicious software will be removed from your computer.
How to Remove Unwanted program from Android/Mobile
To remove an unwanted program virus from your Android phone, follow these simple steps:
Step 1: Start in Safe Mode
First, we'll start your phone in Safe Mode. Safe Mode boots your Android with only the essential apps and settings, preventing malicious apps from interfering.
- Long-press your phone's power button (usually found on the side of your phone) until the power off menu appears.
- When the menu appears, tap and hold the "Power off" button on your screen. You'll see a "Safe mode" option.

- Tap on "Safe mode" to enter it.

- Your phone will restart in Safe Mode, and you'll see the "Safe Mode" text at the bottom left corner of your device.

If you can't find Safe Mode on your phone, you can activate Airplane mode instead to cut off network connections.
Step 2: Check for Malicious Apps with Administrator Privileges
In this step, we'll check if there are any malicious apps with administrator privileges on your phone. These privileges are sometimes used for legitimate purposes but can also be exploited by malicious apps to prevent their removal.
- Tap the "Settings" app on your phone's menu or home screen.
- In the "Settings" menu, look for "Biometrics and Security" (or similar) and then navigate to "Other Security Settings" and "Device admin apps." The location of this option may vary depending on your Android version or phone brand.
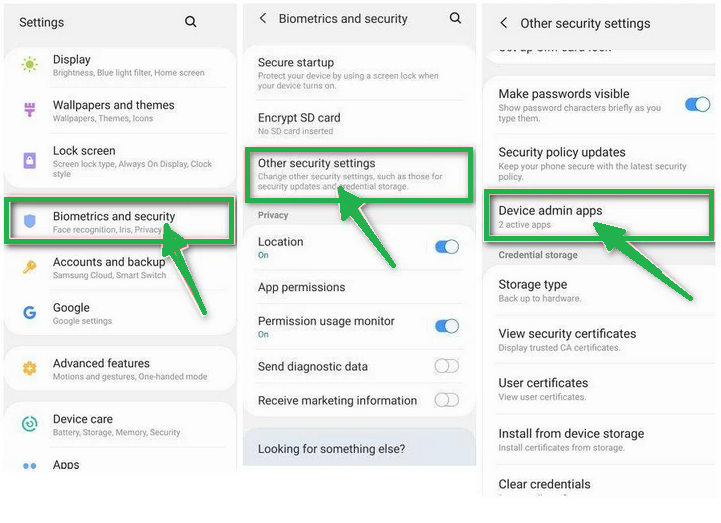
If you can't find "Device admin apps" easily, you can use your phone's search function to look for it.
- Once you're in the list of device admin apps, disable admin rights by tapping the option next to the app. This will remove the checkmark or turn off the toggle button. Some phones also let you tap the app in the admin apps list and then use the "Uninstall" link to remove it immediately.
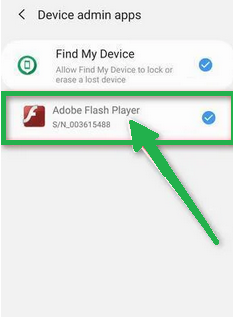
Step 3: Check for Malicious Apps
While your phone is still in Safe Mode, we'll check for malicious apps.
- Tap the "Settings" app.

- In the "Settings" menu, tap on "Apps" or "App Manager" to view all installed applications on your phone.
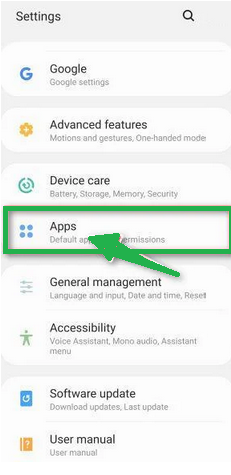
- You'll see a list of all installed apps. Scroll through the list and look for any suspicious apps that you don't remember downloading or that don't seem genuine. Malware is often hidden in apps like photo editors, weather apps, or camera apps.
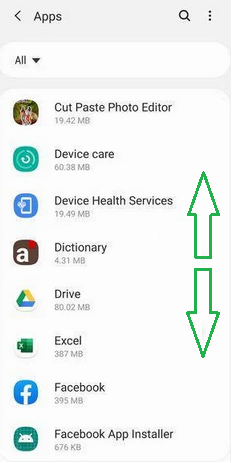
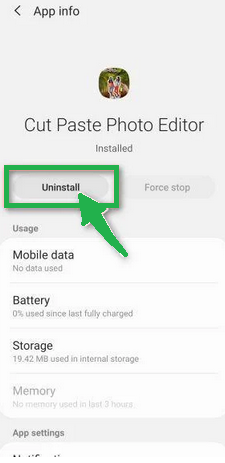
- When you find a suspicious app, tap on it to uninstall. This won't open the app but will take you to the app details screen. If the app is currently running, tap "Force stop," then tap "Uninstall."
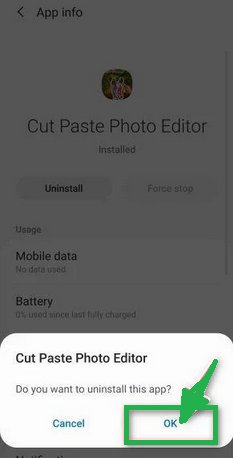
- A confirmation dialog will appear. Tap "OK" to remove the malicious app from your phone.
Step 4: Exit Safe Mode
Now that you've removed the malicious app from your phone, you can exit Safe Mode.
- Hold down the power button until you see the power off menu.
- Select the restart option. Your phone will reboot and exit Safe Mode, returning to normal operation.

By following these steps, you can effectively remove a Unwanted program virus from your Android phone and restore its security.
How to Reset Browsers
How To Reset Chrome to Default Settings
Reset Chrome for Windows
Here's a step-by-step guide to reset Google Chrome on Windows:
- Launch Google Chrome on your computer.
- Look for the three vertical dots in the top right corner of the Chrome window. Click on them to open a menu. Then, select "Settings" from this menu.
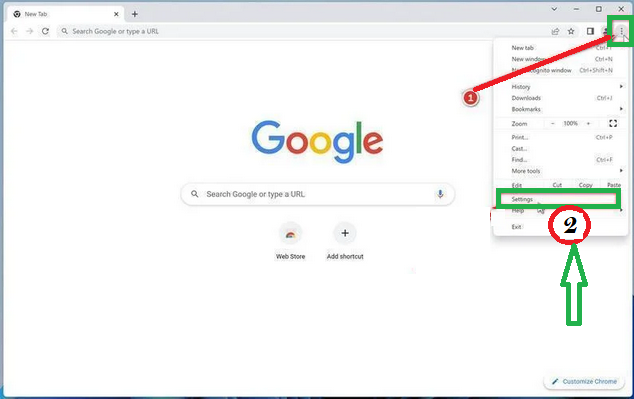
- In the Settings tab that appears, you'll see a sidebar on the left. Click on "Advanced" to get more options.
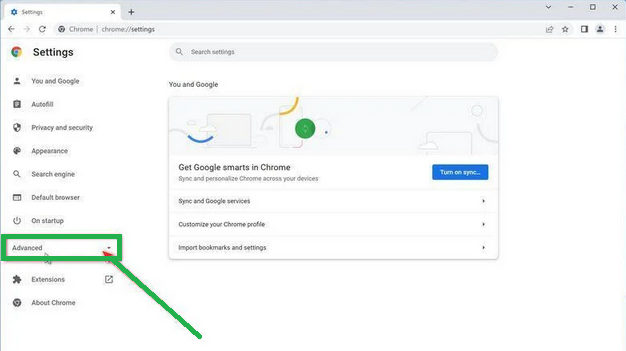
- Under the "Advanced" section in the sidebar, you'll find "Reset and clean up." Click on it.

- Now, in the main part of the window, you'll see the "Reset and clean up" section. Click on "Reset settings to their original defaults."
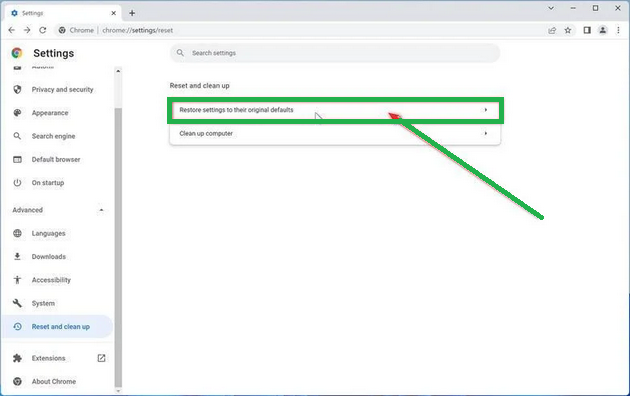
- A window will pop up to confirm the reset. It will explain what will go back to the default settings. If you're okay with that, click on "Reset settings."
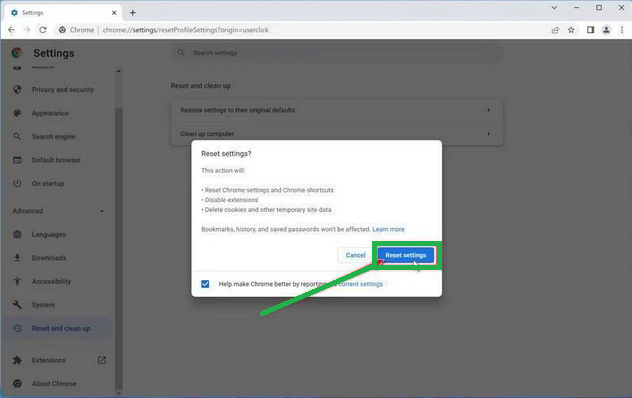
- If you find that a troublesome extension keeps coming back even after the reset, you can reset the data sync. To do this, go to chrome.google.com/sync and click on "Clear Data."

Reset Chrome for Mac
If you're using Google Chrome on a Mac and want to reset it back to its default settings, follow these steps:
- Click on the three dots in the top-right corner of Chrome (the menu button).
- Select "Settings" from the menu that appears. This will open the basic settings screen.

- In the left sidebar, click on "Reset and clean up."

- Now, click on "Reset settings to their original defaults."
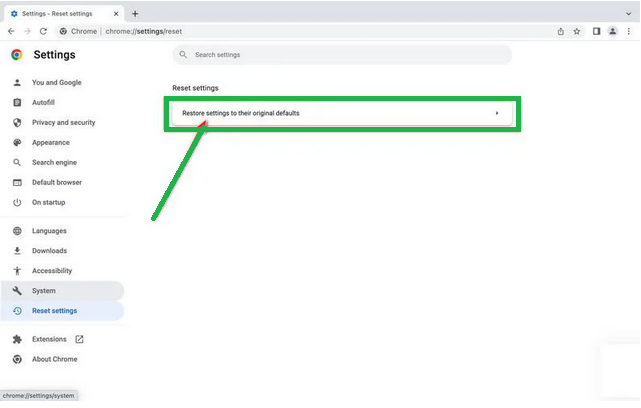
- A confirmation box will pop up, telling you what will be set back to the default settings. To complete the process, click on "Reset Settings."

Keep in mind that doing this will erase your homepage, tab settings, saved information, browsing history, and cookies. It will also disable any extensions you've installed. However, your bookmarks will be safe.
- If you're still having trouble with a malicious extension coming back even after resetting your browser, you can reset your data sync. To do this, go to chrome.google.com/sync and click on the "Clear Data" button.
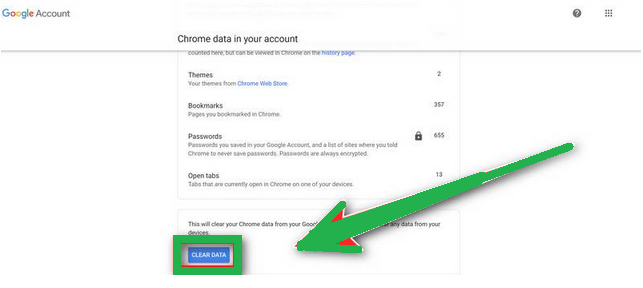
Reset Chrome for Android
Resetting Chrome to its default settings on Android isn't as straightforward as on computers, but it's doable by clearing the app data. This means getting rid of saved cookies, cache, and site settings. Here's how to do it:
- Open the "Settings" app on your Android device. You can usually find it on your home screen or in your phone's app menu.

- In the "Settings" menu, look for "Apps" or "App Manager." This will show you a list of all the apps installed on your phone.

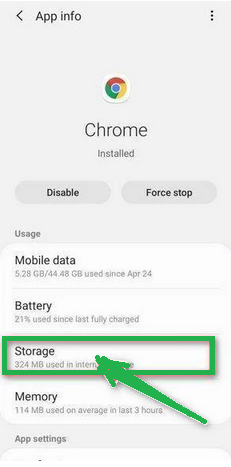
- Scroll through the list until you find the "Chrome" app, and then tap on it to view the app's details.

- Inside Chrome's app info menu, tap on "Storage."
- Under the storage settings, you'll see two options – "Manage Space" and "Clear Cache." Click on "Manage Space."
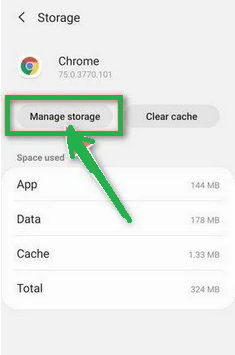
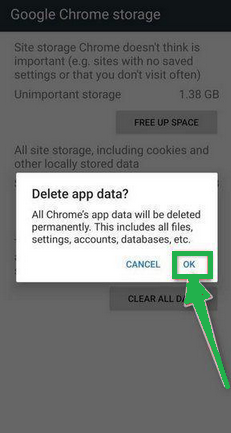
- Now, click on "Clear all Data." This will delete everything related to Chrome, including your accounts, bookmarks, and settings, essentially resetting it to its default state.

- A confirmation message will pop up, explaining what will be reset. To finish the reset process, tap "OK."
How to Reset Internet Explorer
Resetting Internet Explorer is an easy process and only takes a few minutes. Here's how you can do it:
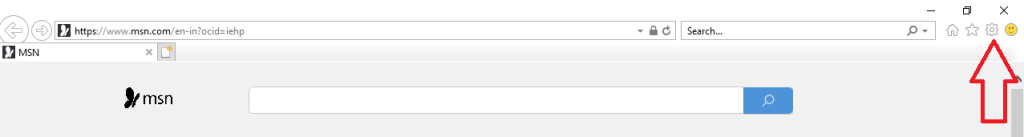
- Open Internet Explorer, which is your web browser.
- Look for a little gear icon in the top-right corner of the browser and click on it.
- Then, select "Internet Options."

- In the "Internet Options" box, click on the "Advanced" tab.
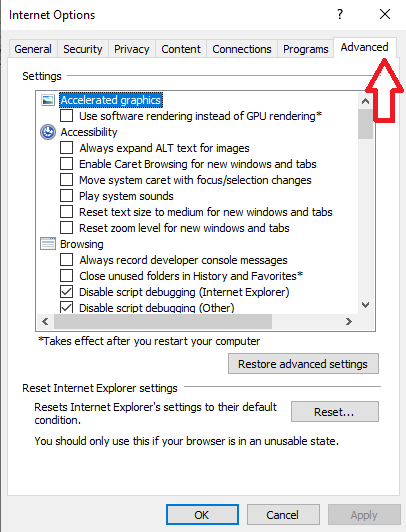
- You'll see a "Reset" button. Click on that.
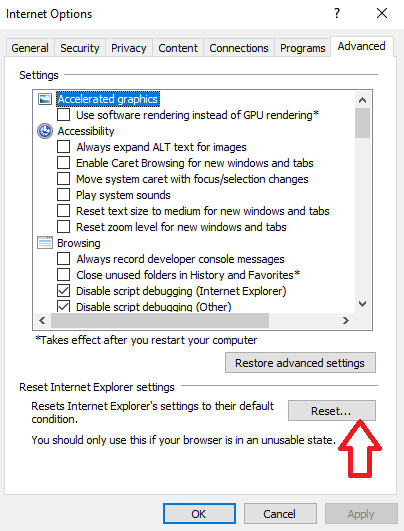
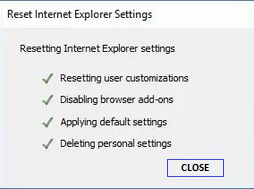
- Now, in the "Reset Internet Explorer settings" section, there's a box that says "Delete personal settings." Check this box, and then click "Reset."

- When Internet Explorer finishes the reset, a message will pop up. Click "Close" to close it. After that, close your browser, and you can open Internet Explorer again.
How To Reset Mozilla Firefox
Reset Firefox for Windows
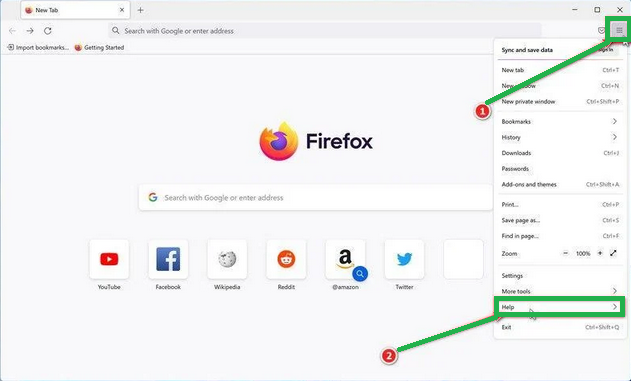
- Click on the three horizontal lines in the top right corner of Firefox to open the menu. Choose "Help" from the menu.
-
- In the "Help" menu, tap on "More troubleshooting information."

- On the "Troubleshooting Information" page, find the "Refresh Firefox" button and click it.
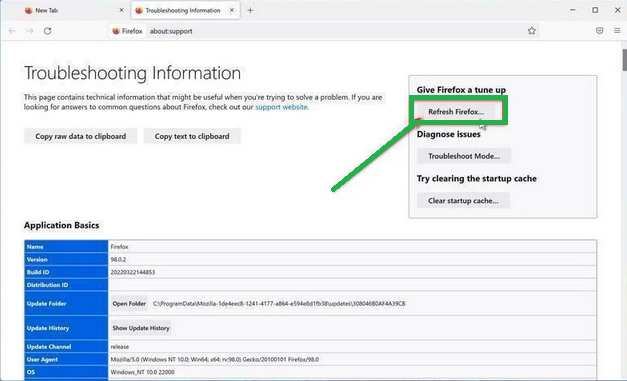
- Confirm the reset by clicking "Refresh Firefox" again in the new window that pops up.

- Firefox will close and go back to its default settings. It will show you what information it saved. Click "Finish" when it's done.
After the reset, you'll see a folder called "Old Firefox Data" on your desktop. It holds your old settings. If the reset didn't solve your problem, you can copy some of the files from this folder to the new profile that was created. But if you're sure you won't need this folder anymore, it's a good idea to delete it since it might contain sensitive information.
Reset Firefox for Mac
Resetting Firefox on a Mac is easy. Here's what you do:
- Click on the three horizontal lines in the top right corner of Firefox to open the menu. Select "Help" from the menu.

- Then, choose "Troubleshooting Information."

- On the Troubleshooting page, you'll see a "Refresh Firefox" button in the upper-right corner. Click on it.
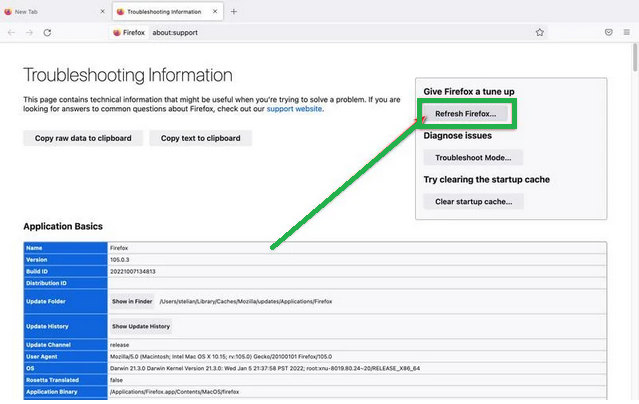
- Confirm the reset by clicking "Refresh Firefox" again in the new window.
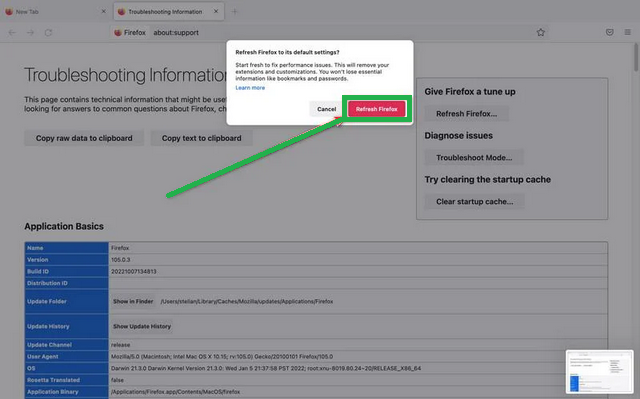
- Firefox will close and go back to its default settings. It will show you what information it saved. Click "Finish" when it's done.
That's it! Resetting Firefox on your Mac is a quick way to make it work better while keeping your important data safe.
Reset Firefox for Android
Resetting Firefox to its default settings on Android is a bit different but still doable. It involves clearing the app's data, which includes cookies, cache, and saved site settings. Here's how you can do it:
- Open your phone's "Settings" app, which you can find in your menu or on the home screen.
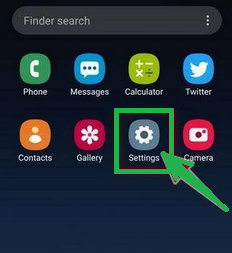
- In the "Settings" menu, look for "Apps" or "App Manager." This will show you all the apps installed on your phone.
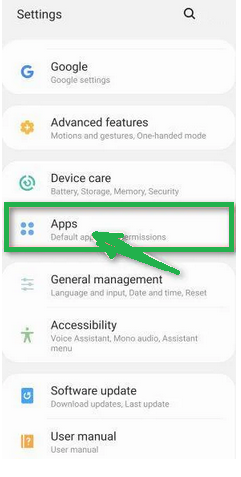
- Scroll through the list of apps until you find "Firefox." Click on it to open the app's details.

- In Firefox's app menu, click on "Storage."

- In the storage settings, you'll see two options: "Manage Space" and "Clear Cache." Click on "Manage Space."

- Now, click on "Clear all data." This will delete all of Firefox's data, including your accounts, bookmarks, and settings, effectively resetting it to its default state.

- You'll see a confirmation message that explains what will be reset. To complete the reset, tap "Ok."
How To Reset Edge to Default Settings
To reset Microsoft Edge on your computer, follow these simple steps:
- Click on the three horizontal dots in the top-right corner of Microsoft Edge to open the menu. From the menu, select "Settings."

- Tap "Reset Settings" on the left side of the window.

- Now, click on "Restore settings to their default values" in the main window.
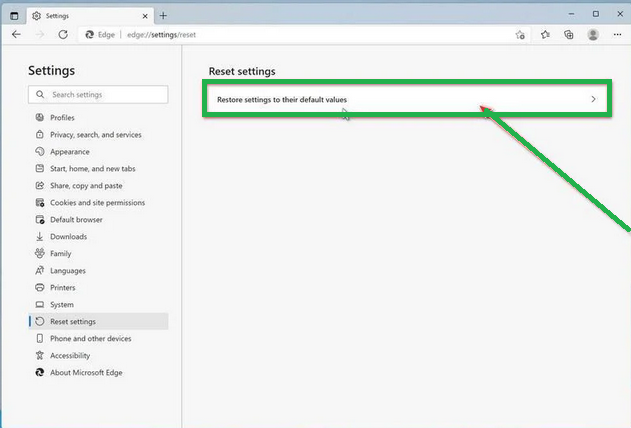
- A confirmation message will appear, explaining what will be reset. To proceed, click "Reset."
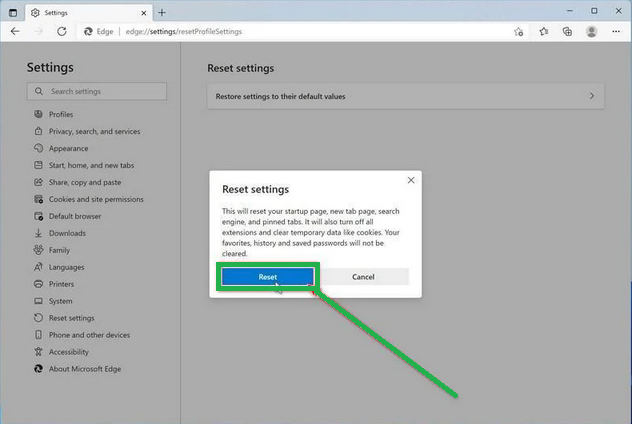
- Microsoft Edge will erase your personal data, browsing history, and disable any installed extensions. But don't worry, your bookmarks will remain safe and accessible.
How To Reset Safari
Before resetting Safari to its default settings, if you have bookmarks you want to keep, open Safari, go to the "File" menu, and choose "Export Bookmarks." Give your backup a name and save it.
To reset Safari on a Mac, you can use the Settings menu or Terminal. If you're using Safari on an iPhone or iPad, tap the iOS tab to reset the settings. This way, you won't lose your important bookmarks when you reset Safari. It's like making a copy of your bookmarks before cleaning up your browser.
Reset Safari for Mac via Settings
Here's how to reset Safari:
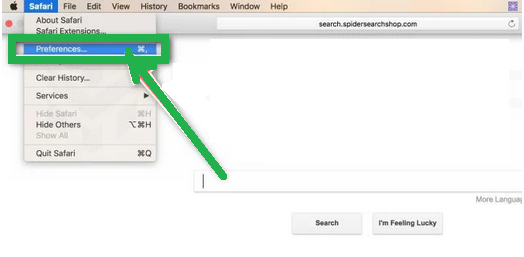
- Click "Safari" in the menu, then choose "Preferences." This opens a new window with your Safari settings.
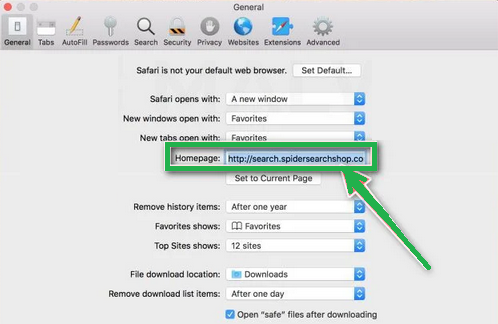
- Check your homepage in the "General" tab. If it's not what you want, change it.
- Next, click on the "Extensions" tab.

- Look for any extensions you don't remember installing or seem suspicious. It's usually safe to remove them.

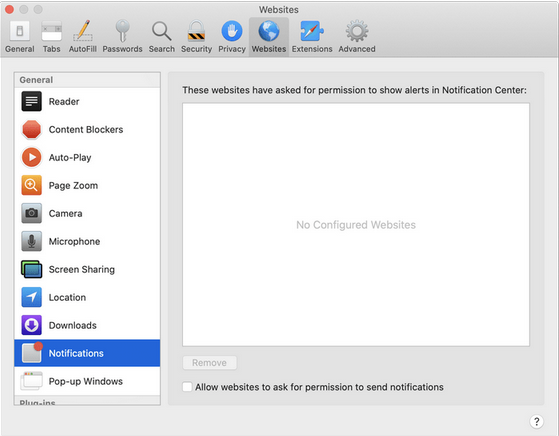
- In "Preferences," go to "Websites" and then "Notifications." Turn off the option that allows websites to ask for push notifications.
- In the Safari menu, choose "Preferences" again, then go to "Privacy." Tap on "Manage Website Data".
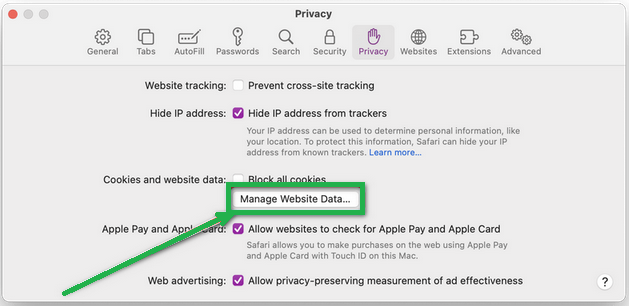
- Choose "Remove All" to clear website data.
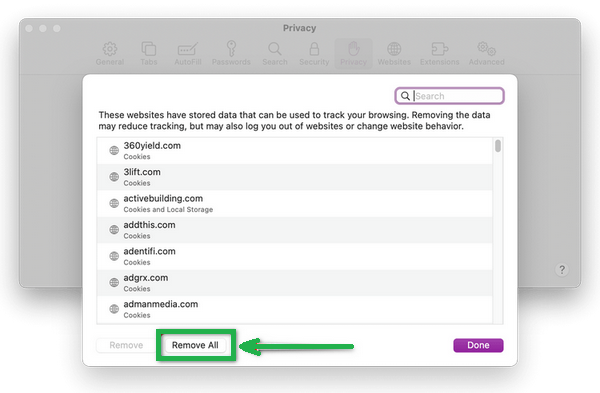
- To show the "Develop" menu, go to the "Advanced" tab in "Preferences" and enable "Show Develop menu in menu bar."
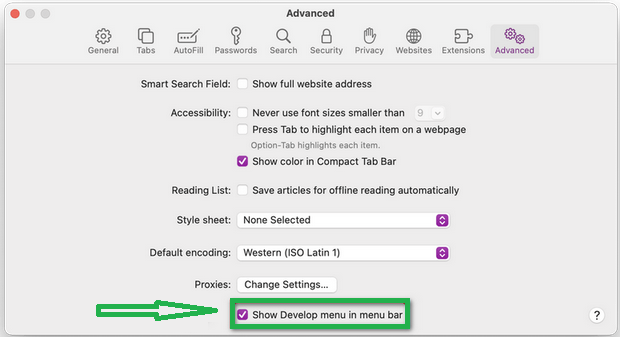
- Click on "Develop" in the menu bar, and then select "Empty Caches" to clear out temporary files.
Reset Safari for Mac via Terminal
To reset Safari on your Mac, follow these steps:
- Open the "Terminal" app (you can search for it using Spotlight with "Cmd + Space").
- Go to the Apple menu at the top-left and choose "Force Quit." Select "Safari" to close it completely.
- Enter the commands one by one in Terminal. It will ask for confirmation to delete files. Type "y" and press "Enter" after each command.
mv ~/Library/Safari ~/Desktop/Safari-`date +%Y%m%d%H%M%S`;
rm -Rf ~/Library/Cache/*;
rm -Rf ~/Library/Caches/Apple\ -\ Safari\ -\ Safari\ Extensions\ Gallery;
rm -Rf ~/Library/Caches/Metadata/Safari;
rm -Rf ~/Library/Caches/com.apple.Safari;
rm -Rf ~/Library/Caches/com.apple.WebKit.PluginProcess;
rm -Rf ~/Library/Cookies/*;
rm -Rf ~/Library/Cookies/Cookies.binarycookies;
rm -Rf ~/Library/Preferences/Apple\ -\ Safari\ -\ Safari\ Extensions\ Gallery;
rm -Rf ~/Library/Preferences/com.apple.Safari.LSSharedFileList.plist;
rm -Rf ~/Library/Preferences/com.apple.Safari.RSS.plist;
rm -Rf ~/Library/Preferences/com.apple.Safari.plist;
rm -Rf ~/Library/Preferences/com.apple.WebFoundation.plist;
rm -Rf ~/Library/Preferences/com.apple.WebKit.PluginHost.plist;
rm -Rf ~/Library/Preferences/com.apple.WebKit.PluginProcess.plist;
rm -Rf ~/Library/PubSub/Database;
rm -Rf ~/Library/Safari/*;
rm -Rf ~/Library/Safari/Bookmarks.plist;
rm -Rf ~/Library/Saved\ Application\ State/com.apple.Safari.savedState;
Reset Safari for iOS (iPhone or iPad)
To reset Safari on your iPhone or iPad, follow these steps:
- Open the "Settings" app.

- Turn on "Airplane Mode" to disconnect from the internet temporarily and block unwanted access.
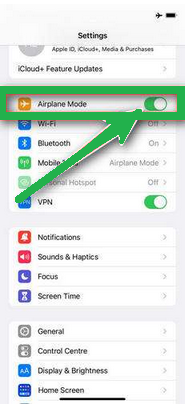
- Scroll down and click on "Safari."
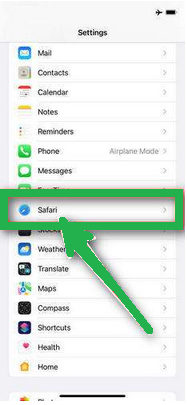
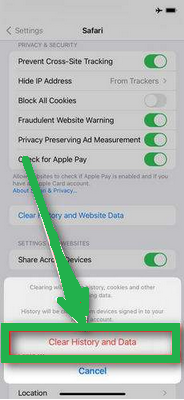
- Now, choose "Clear History and Website Data."

- Confirm by tapping "Clear History and Data" in the pop-up window.
- While in Safari settings, make sure to turn on "Block Pop-ups" and "Fraudulent Website Warning."
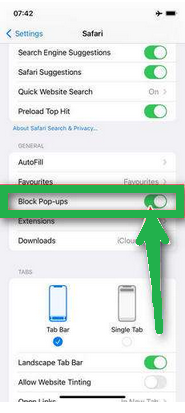
These steps clear your browsing history, website data, and other information stored by websites you visited. Also, by enabling "Block Pop-ups" and "Fraudulent Website Warning," you can enhance your browsing experience and protect yourself from unwanted ads and potentially harmful websites.
Recommended Security Software (SpyHunter)
SpyHunter acts like a guardian for your computer, shielding it from nasty stuff like malware and spyware. Using smart scanning, it hunts down and kicks out harmful programs sneaking around your system. It’s not just a detective; it also stops new threats from barging in. Anyone, whether tech-savvy or not, can easily use it because of its simple design. Plus, it keeps learning and gets regular updates to stay ahead of the bad guys. If you want a solid defender for your PC against digital troublemakers, SpyHunter is a reliable choice, always ready to keep your computer safe.
Step 1: Download SpyHunter 5 for your device through the provided link. Obtain it by clicking below.
Step 2: Proceed to the location where the installer is saved in your system. Typically, the file is stored in the “Downloads” directory. Execute the setup process by double-clicking on the installer file.
Step 3: Choose your desired language and press the “OK” button. This action triggers the installer initialization. When prompted, click the “Continue” button to proceed with the installation process.

Step 4: During installation, you’ll encounter a prompt to approve the ‘EULA and Privacy Policy.’ Opt for ‘I accept the EULA and Privacy Policy’ and then select the ‘Accept & Install’ button. This step is necessary to proceed with the installation process of the application.
Step 5: Initiate the installation process, and observe the progression through the visible progress bar. The process may require some time for completion. Once finished, a notification confirming successful installation will be displayed.

Step 6: Upon installation completion, SpyHunter will automatically launch. The following screen will be displayed for your attention.

Step 7: Additionally, the scanner will initiate a comprehensive scan of your computer to identify potential threats within your device. Throughout the scan, it will present you with information such as the detected threat’s name, security level, and specific details about the threat. Relax and wait for the scan process to conclude.
Step 8: Upon completion of the scan, press the “Next” button to continue the process.
Step 9: To finalize the removal process, the application will prompt you to purchase its licensed version. Alternatively, you have the option to opt for a 7-day free trial, during which the software will be fully operational, allowing you to eliminate all identified threats.
Special Offer
In order to remove VolfDex.com hassle free, we suggest you to scan the PC with powerful SpyHunter antimalware scanner. The fully functional free Trial of SpyHunter is Available for 7 days (Windows Version) with Credit Card required. There are no upfront charges within this period. Further, no charge will apply if you cancel 2 business days before the trail ends. For Mac Users, it is suggested to use Combo Cleaner which is a powerful antivirus and System optimizer.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
FAQs about VolfDex.com Scam
In what ways do VolfDex.com scammers carry out their scheme?
Scammers trick victims by asking for fees, insisting on deposits to fix account problems, tempting with partial withdrawals, and disappearing after taking as much money as they can.
What unfolds after a victim sets up an account?
Scammers, posing as customer service reps, contact victims through email or chat apps. They build trust and persuade victims to deposit more money by giving instructions on funding accounts with cryptocurrencies or payments.
What causes the delay and prevention of withdrawals?
Scammers use tactics like placing holds and making up reasons to delay withdrawals. This prolongs the scam, tricking victims into depositing more money. The scammers have no intention of actually paying out any earnings.
Is it possible for victims to reclaim or retrieve funds post-scam?
Sadly, victims rarely recover lost money due to the anonymous nature of crypto payments and the absence of regulations. Once money is deposited, it becomes extremely challenging to retrieve.
What steps can I take to steer clear of cryptocurrency investment scams similar to VolfDex.com?
Watch out for promises of guaranteed profits, urgent demands, and unexpected contacts. Before sharing personal information or money, thoroughly investigate any opportunity. If it seems too good to be true, it probably is.
To sum it up, this article delves into the VolfDex.com crypto scam, outlining its modus operandi, identification methods, targeted social media platforms, preventive measures, and steps to take if one has already fallen victim. It provides a comprehensive overview of the scam, offering insights on recognizing red flags, avoiding potential traps, and taking corrective actions. The information spans from understanding the scam’s mechanics to safeguarding oneself through awareness and proactive steps. By addressing the entire spectrum from awareness to response, the article equips readers with the knowledge needed to navigate the complexities of the VolfDex.com crypto scam and protect themselves in the evolving landscape of online fraud.