How to Remove Jawr Ransomware: Safely Eliminating Malware and Recovering Encrypted Files

All About Jawr Ransomware
Jawr Ransomware is a harmful computer program made by bad people who want money. This software locks your important files by turning them into secret codes, and you can only get them back if you pay them money. Jawr is a kind of hazardous threat that encrypts personal files, changing their names to end with “.jawr,” and then asks for payment in cryptocurrencies for unlocking them.
When it’s done with file encryption, Jawr also creates a note called “_readme.txt.” In this note, the bad people tell you that your files, like pictures and documents, are now secret-coded using a strong method, and only they have the special key to unlock them. They suggest a solution to get your files back, which involves buying a special tool and a unique key from them.
To prove they can help, the attackers offer to unlock one file for free, but it should not be something important. The note mentions that if you contact them within 72 hours, they will give you a discount, asking for $490 instead of the regular $980.
They warn that you can’t get your files back without paying, and they provide email addresses (support@freshmail.top and datarestorehelpyou@airmail.cc) for you to contact them.
Straightforwardly, Jawr Ransomware is a program that encrypts your files and asks for money to unlock them. Attackers tell you how much to pay, offer a discount if you’re quick, and say you can’t get your files back unless you pay them. It’s important to understand these things to stay safe from such cyber threats.
Message in the Ransom Note:
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-iu965qqEb1
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
support@freshmail.top
Reserve e-mail address to contact us:
datarestorehelpyou@airmail.cc
Your personal ID:
–
In what manner does Ransomware execute its attacks?
Jawr Ransomware is like a sneaky intruder that finds three secret ways to get into your computer without you knowing. First, it often hides in emails that look harmless but actually carry the bad software. If you open these emails and their attachments, you let the bad code inside, and it starts causing trouble.
The second way is through old and not-updated computer programs. The crooks behind Jawr know about problems in these programs and use them to break into your device. To avoid this, it’s important to regularly update your programs, like your computer’s software, to close these security gaps.
The third method is a bit like going to a risky neighborhood on the internet. Sometimes, when you click on ads or visit insecure websites, you might unknowingly download malicious software. Once it’s on your system, it starts the ransomware, locking up your files.
To protect yourself, you need to be part of the solution. This means being careful about opening emails from unknown sources, always updating your computer programs, and using strong security software that can stop ransomware attacks.
While Jawr Ransomware might catch you off guard, understanding how it sneaks in gives you a chance to make your PC safer. By staying ahead and being watchful, you don’t just use technology – you also make sure it’s safe from bad threats like Jawr Ransomware. So, be smart, stay updated, and keep your digital world secure.
What actions can be taken in advance to stop Ransomware?
When dealing with the potential threat of Jawr Ransomware, it’s crucial to go beyond the basics and implement specific, practical measures to strengthen your computer’s defenses. While avoiding suspicious emails and keeping your software up-to-date are important, there are additional steps that can plug potential gaps left by these initial precautions.
Firstly, use features like User Account Control (UAC) on Windows or Gatekeeper on MacOS – they’re like strong walls stopping bad software. Don’t do everyday things on an account with administrative powers; it’s risky. Instead, create a normal account for regular stuff. This way, if something bad tries to sneak in, it’s harder for it to cause trouble. Keep the important stuff safe by using these features – it’s like having guards for your computer!
Secondly, always back up your data! Sometimes bad things can happen to your computer, like Jawr Ransomware getting in. Having a backup means you have a safe copy of all your important stuff. Use tools like Windows’ File History or MacOS’s Time Machine for backups on your computer. You can also use services like Backblaze or Carbonite for extra safety by storing backups in the cloud. This way, if something goes wrong, you can always get your important files back.

The third strategy is to be smart about emails! Jawr Ransomware often comes through sneaky emails. Learn to spot them to stay safe. Look out for emails with basic greetings, bad grammar, spelling mistakes, or those asking for personal info urgently. If you notice these things, it could be a trick. Don’t open or click anything suspicious. Being careful with emails helps keep your computer safe from Jawr Ransomware and other bad stuff.
Enabled macros, a type of tool in common applications, are a known weakness against ransomware. Strengthen your system by disabling macros or setting them to run in ‘disable all’ mode, but make exceptions only if you trust where things come from.
Last but not least, use tools like Software Restriction Policy (SRP) or App Locker on Windows. These tools control which software is allowed, giving strong protection against harmful programs. It’s like having guards deciding what’s allowed in your computer to keep it safe from bad stuff.
In essence, by taking these extra steps – creating strong barriers, maintaining secure backups, being vigilant against phishing, managing macros, and implementing software restrictions – you build a robust defense against the potential threats posed by Jawr Ransomware. It’s like adding extra layers of armor to your digital fortress, ensuring a safer and more secure computing experience.
Ransomware Removal Process
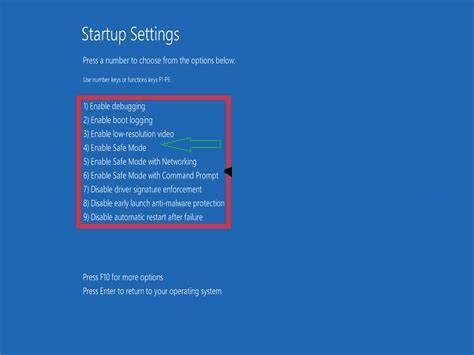
Step 1: Enable Safe Mode
Removing Jawr Ransomware from your system is a critical task that requires a methodical approach. One of the initial steps in this process is booting your PC in Safe Mode. Safe Mode is a diagnostic mode in which the operating system loads only essential components, helping to isolate and remove malicious software like ransomware. The procedure for entering Safe Mode varies slightly depending on the Windows version you have.
For Windows XP and Windows 7 users, start by clicking on the “Start” button and continually press the F8 key during the boot process until the “Windows Advanced Options” menu shows up. Use the arrow keys to select the appropriate Safe Mode option and press Enter to initiate the boot process in Safe Mode.

Windows 8 users can access Safe Mode by first going to the “Start Screen” and selecting “Settings” from the search results. Type “Advanced” and pick “Advanced startup” in the “General PC Settings” menu. Click “Restart Now” and navigate to “Troubleshoot,” then “Advanced options,” and finally “Startup Settings.” After clicking “Restart,” press the F5 key when prompted to boot into Safe Mode.
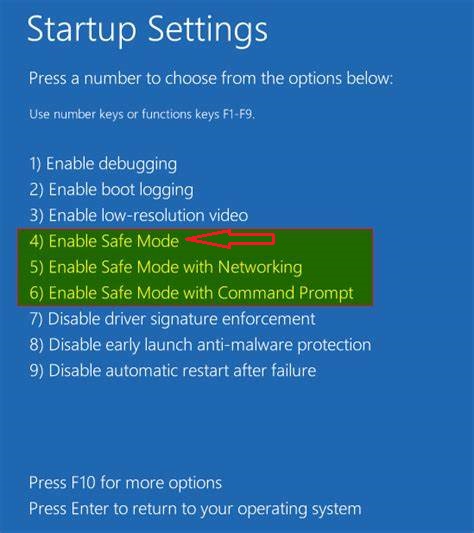
Windows 10 users should press the Windows logo as well as the Power icon, select “Restart” while holding the “Shift” key. In the “Choose an option” window, click on “Troubleshoot,” then “Advanced Options,” and choose “Startup Settings.” Click “Restart,” and in the subsequent window, press the F5 key to boot into Safe Mode.
In Safe Mode, your computer will operate with minimal functionalities, allowing you to conduct a more focused and effective ransomware removal process. This secure environment reduces the chances of the ransomware interfering with your efforts, providing a better chance of successful removal. Once in Safe Mode, you can proceed with additional steps to analyze and eliminate the Jawr Ransomware from your system.
Step 2: System Restore
If you can’t start your PC in Safe Mode, an alternative is to use “System Restore” to roll back your system to a point before Jawr Ransomware infected it.
Start by pressing the F8 key during startup until the “Advanced Options” menu appears. Choose “Safe Mode with Command Prompt” and press Enter.
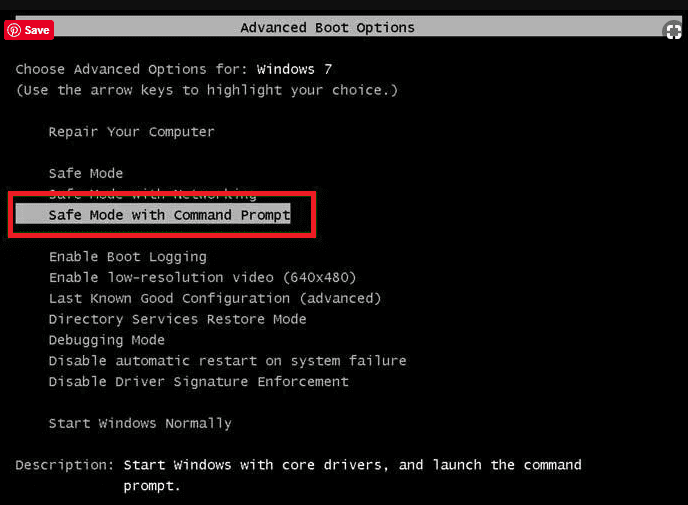
In the Command Prompt, type “cd restore” and hit Enter.
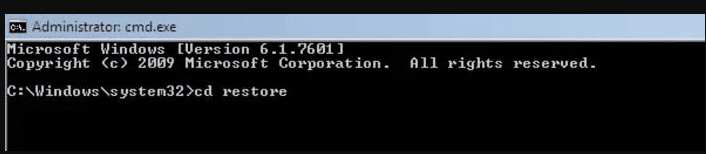
Then, type “rstrui.exe” and hit Enter.

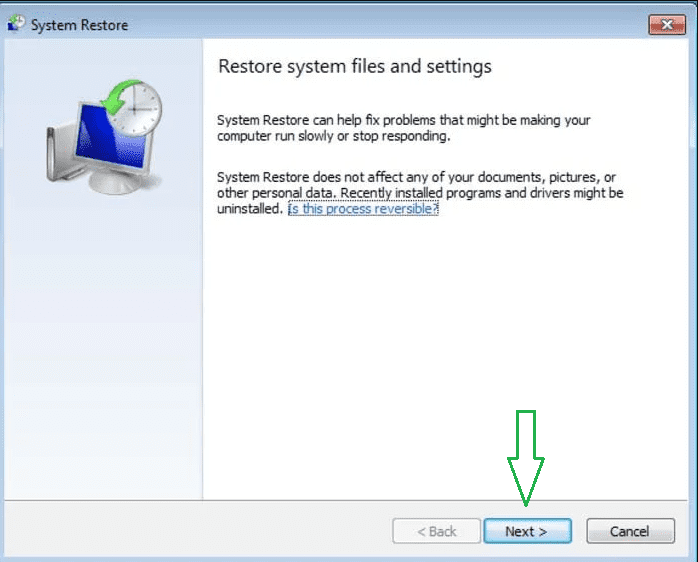
Follow the prompts.
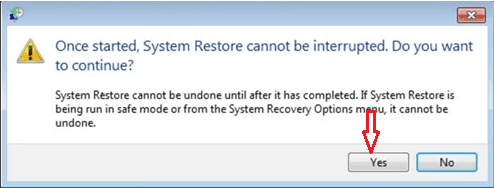
Select a restore point before the ransomware attack, and click “Next.”
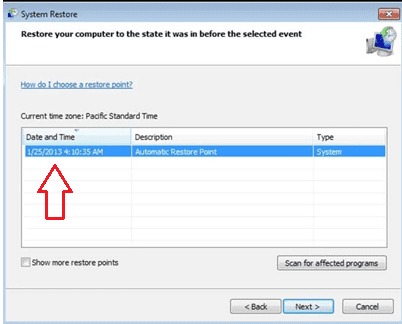
Confirm your choice by clicking “Yes.” This process reverts your system to a state before Jawr Ransomware compromised it, helping to eliminate the malware.
Step 3: Malware Removal Tool
After restoring your computer to a previous state, download and use the SpyHunter anti-malware tool. Run a thorough scan to detect and remove any remaining Jawr Ransomware files on your device, ensuring comprehensive removal of the malware.
Recommended Security Software (SpyHunter)
SpyHunter acts like a guardian for your computer, shielding it from nasty stuff like malware and spyware. Using smart scanning, it hunts down and kicks out harmful programs sneaking around your system. It’s not just a detective; it also stops new threats from barging in. Anyone, whether tech-savvy or not, can easily use it because of its simple design. Plus, it keeps learning and gets regular updates to stay ahead of the bad guys. If you want a solid defender for your PC against digital troublemakers, SpyHunter is a reliable choice, always ready to keep your computer safe.
Step 1: Download SpyHunter 5 for your device through the provided link. Obtain it by clicking below.
Step 2: Proceed to the location where the installer is saved in your system. Typically, the file is stored in the “Downloads” directory. Execute the setup process by double-clicking on the installer file.
Step 3: Choose your desired language and press the “OK” button. This action triggers the installer initialization. When prompted, click the “Continue” button to proceed with the installation process.

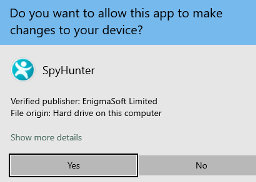
Step 4: During installation, you’ll encounter a prompt to approve the ‘EULA and Privacy Policy.’ Opt for ‘I accept the EULA and Privacy Policy’ and then select the ‘Accept & Install’ button. This step is necessary to proceed with the installation process of the application.
Step 5: Initiate the installation process, and observe the progression through the visible progress bar. The process may require some time for completion. Once finished, a notification confirming successful installation will be displayed.

Step 6: Upon installation completion, SpyHunter will automatically launch. The following screen will be displayed for your attention.

Step 7: Additionally, the scanner will initiate a comprehensive scan of your computer to identify potential threats within your device. Throughout the scan, it will present you with information such as the detected threat’s name, security level, and specific details about the threat. Relax and wait for the scan process to conclude.
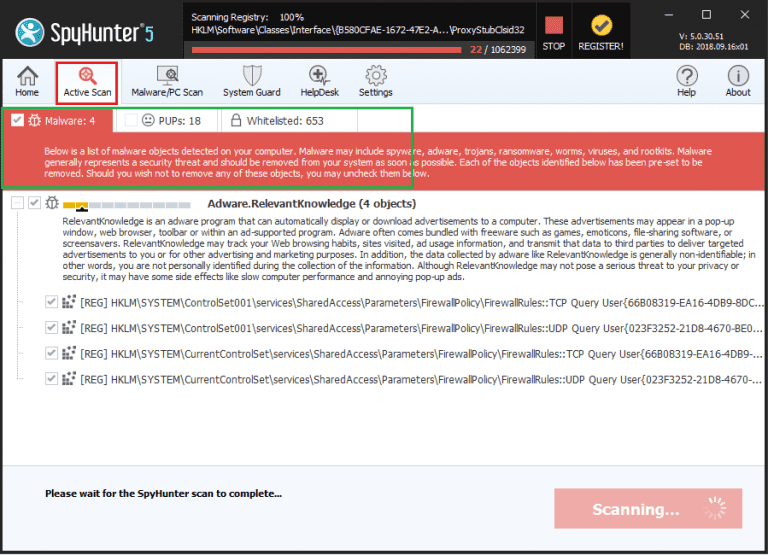
Step 8: Upon completion of the scan, press the “Next” button to continue the process.
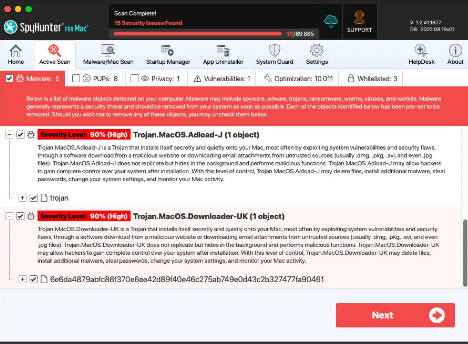
Step 9: To finalize the removal process, the application will prompt you to purchase its licensed version. Alternatively, you have the option to opt for a 7-day free trial, during which the software will be fully operational, allowing you to eliminate all identified threats.
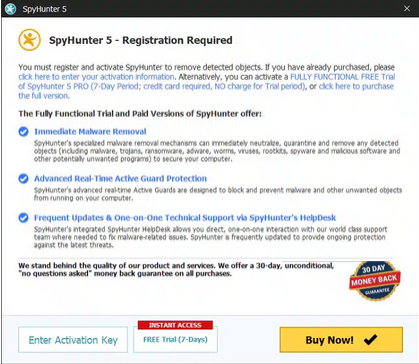
Special Offer
In order to remove Jawr Ransomware hassle free, we suggest you to scan the PC with powerful SpyHunter antimalware scanner. The fully functional free Trial of SpyHunter is Available for 7 days (Windows Version) with Credit Card required. There are no upfront charges within this period. Further, no charge will apply if you cancel 2 business days before the trail ends. For Mac Users, it is suggested to use Combo Cleaner which is a powerful antivirus and System optimizer.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
What measures can be taken to recover files after a ransomware attack?
If your files are locked by ransomware, the first step is to check for backups to restore and recover your data. Start by looking for off-site or offline backups, like those stored in the cloud, as they remain untouched during the attack. Additionally, check for Volume Shadow copies on your Windows system, although many ransomware strains delete them.
Inspect on-site backups, even though attackers often target and delete or encrypt local data. If backups are unavailable, consider recreating the data using various methods. First, recreate data from physical hard copies – manually input information from printed documents into your computers and servers. This approach is reliable but time-consuming.
Retrieve data from email exchanges, focusing on saved attachments. Emails can serve as a valuable source to recover important information. Another method involves database mining, where some ransomware variants encrypt only a portion of a database or backup file, allowing extraction of valid and usable data.
While dealing with the aftermath of a ransomware attack can be challenging, a combination of backup restoration and creative data recreation methods increases the chances of recovering crucial information. Always prioritize securing and regularly updating your backups to minimize the impact of potential future ransomware incidents.
Use Stellar Data Recovery to Recover Files
If you’ve exhausted traditional recovery methods after a ransomware attack, consider using the Stellar Data Recovery tool. This user-friendly software helps retrieve lost or encrypted files. Simply download and install the tool, select the drive or location where your files were stored, and let Stellar scan for recoverable data. Once the scan is complete, preview and choose the files you want to restore. Stellar’s straightforward interface makes it a reliable choice for recovering files when other methods have failed, providing an additional option to regain access to your important data after a ransomware incident.