How to Remove Jazi Ransomware: Strategies for Removal and Data Recovery

About Jazi Ransomware
Jazi is a nasty kind of ransomware, part of the STOP/Djvu ransomware family, that messes with your computer and demands money. It targets your important files, like documents and photos, by locking them up until you pay a ransom. This virus doesn’t care about the type of files; it can mess with everything from pictures to audio files. Jazi is tricky – it won’t touch system folders, so you might not notice the damage until it’s too late. It adds “.jazi” to your files to show they’re infected, and after it’s done messing things up, it leaves a scary note called “_readme.txt.”
The note is all about urgency, saying your files are locked up with super-strong encryption. The attackers demand $980, but if you pay within 72 hours, they’ll cut it to $490. They even offer a video showing how to get your files back. But here’s the catch – paying them is a bad idea. It’s like giving in to bullies, and there’s no guarantee you’ll get your files back.
Instead, experts say to disconnect your computer from the internet, scan for viruses, and talk to cybersecurity pros for safer ways to get your files back. This puts your security first and helps break the cycle of these bad guys getting paid. Jazi is serious trouble for your PC, but you can fight back by acting fast and using anti-malware tools to kick it out. These tools are like superhero software made to find and remove Jazi Ransomware, making your whole system safer. So, if you’re facing Jazi, don’t panic – take action and get the right tools to protect your device.
Text in the Ransom Note:
ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-iu965qqEb1
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
support@freshmail.top
Reserve e-mail address to contact us:
datarestorehelpyou@airmail.cc
Your personal ID:
–
Jazi Ransomware is a dangerous type of software that can take over your computer, encrypt your files, and demand money for their release. This is a major concern for both individuals and businesses, as it poses a serious threat to your data and system. Understanding how Jazi Ransomware works is crucial for protecting your device from such malicious attacks in today’s ever-changing world of cyber threats.
This tutorial seeks to offer a thorough insight into Jazi Ransomware, delving into its operations and the potential dangers it presents to your system. Additionally, it examines reliable methods for detecting and identifying ransomware, empowering informed decision-making in the face of a possible attack. Equipping ourselves with ample knowledge allows us to counteract this digital threat and safeguard our data and systems effectively.
Detecting and Defending Against Ransomware: A Practical Guide

In the ever-evolving landscape of cybersecurity, staying ahead of ransomware threats like Jazi requires a combination of sharp observation and effective tools. Here’s a simple guide in points to equip yourself with essential knowledge and increase your chances of detection:
- File Extension Modifications and File Access Impediment:
- Monitor your files vigilantly for sudden changes in file extensions.
- Inability to open files or access certain documents may indicate Jazi’s encryption capabilities.
- Keep an eye out for unexpected alterations in your file structure.
- Desktop Wallpaper Changes:
- Watch for changes in your desktop wallpaper, as ransomware like Jazi often displays a ransom note.
- An altered wallpaper is a clear sign that something unusual has happened to your system.
- Be wary of any prompts or messages demanding payment for file access.
- Surprise Network Data Activity:
- Use network monitoring tools to observe inbound and outbound traffic.
- Look for substantial unexplained outbound traffic, which could indicate data being siphoned off.
- Detecting unusual data packets over your network is a red flag for an active ransomware attack.
- Atypical CPU and Disk Utilization:
- Regularly check your Task Manager for high CPU and disk usage by unfamiliar applications.
- Jazi Ransomware may disguise itself as a legitimate system service, making detection more challenging.
- Seasoned tech users are advised to stay vigilant and identify suspicious activity promptly.
- Degraded System Operational Efficiency:
- While slow system performance can have various causes, sudden and significant reductions may signal Jazi’s presence.
- Ransomware often burrows deep into the system, consuming excessive processing power.
- Monitor system responsiveness and speed for any abrupt declines.
- Disruption of Security Tools:
- Regularly validate the functionality of your antivirus and firewall software.
- Ransomware, including Jazi, may attempt to disable security measures to carry out its malicious activities.
- Any unexpected changes to your security software’s status should raise immediate concerns.
- Deploy Ransomware Detection Software Safeguard:
- Employ specialized ransomware detection tools to scan, detect, and remove threats like Jazi.
- Update these tools regularly to protect against the latest ransomware strains.
- Ensure that the detection tool covers a wide range of ransomware variants for comprehensive defense.
The key to identifying and defending against Jazi Ransomware lies in a combination of vigilance and the right tools. Regularly monitor file changes, network traffic, and system performance while staying alert to unexpected alterations in your security software. By employing these simple yet effective measures, you can enhance your ability to detect and mitigate the impact of Jazi Ransomware on your digital environment.
Jazi Ransomware Removal
Dealing with the Jazi Ransomware requires a strategic approach to safely remove the threat and restore your system’s functionality. As technology enthusiasts, let’s harness the power of technology to combat this menace effectively.
Step 1: Disconnecting Internet Connection

Contrary to common intuition, the initial step involves disconnecting from the internet. Ransomware, like Jazi, often relies on an internet connection to control and propagate within the compromised system. By going offline, you disrupt the malware’s communication, putting a halt to further data encryption and potential damage.
Step 2: Pinpointing the Offender

To effectively combat Jazi Ransomware, it’s crucial to identify the specific variant affecting your system. While we’re focusing on Jazi, different variants may operate in unique ways. Utilize offline tools, such as ID ransomware, for accurate detection. Understanding the specific ransomware variant is essential for employing the right removal techniques.
Step 3: Isolation and Quarantine

Isolate the affected devices from the rest of your network to prevent the ransomware from spreading. This involves disconnecting shared or networked drives. Ransomware can easily hop across networks, so swift quarantine is vital to contain the threat and protect other devices.
Step 4: Malware Removal

Moving forward, remove Jazi Ransomware using reputable, offline antivirus tools. Ensure that these tools are updated with the latest definitions to effectively detect and remove the threat. Additionally, consider using specialized ransomware removal tools designed specifically for combating threats like Jazi.
Recommended Security Software (SpyHunter)
SpyHunter acts like a guardian for your computer, shielding it from nasty stuff like malware and spyware. Using smart scanning, it hunts down and kicks out harmful programs sneaking around your system. It’s not just a detective; it also stops new threats from barging in. Anyone, whether tech-savvy or not, can easily use it because of its simple design. Plus, it keeps learning and gets regular updates to stay ahead of the bad guys. If you want a solid defender for your PC against digital troublemakers, SpyHunter is a reliable choice, always ready to keep your computer safe.
Step 1: Download SpyHunter 5 for your device through the provided link. Obtain it by clicking below.
Step 2: Proceed to the location where the installer is saved in your system. Typically, the file is stored in the “Downloads” directory. Execute the setup process by double-clicking on the installer file.
Step 3: Choose your desired language and press the “OK” button. This action triggers the installer initialization. When prompted, click the “Continue” button to proceed with the installation process.

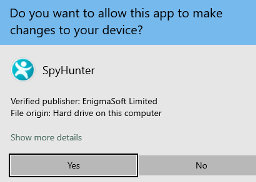
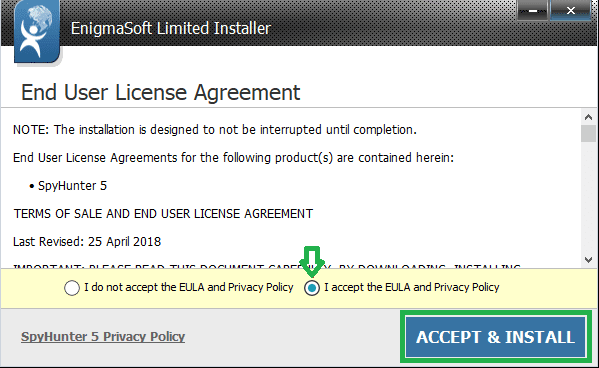
Step 4: During installation, you’ll encounter a prompt to approve the ‘EULA and Privacy Policy.’ Opt for ‘I accept the EULA and Privacy Policy’ and then select the ‘Accept & Install’ button. This step is necessary to proceed with the installation process of the application.
Step 5: Initiate the installation process, and observe the progression through the visible progress bar. The process may require some time for completion. Once finished, a notification confirming successful installation will be displayed.

Step 6: Upon installation completion, SpyHunter will automatically launch. The following screen will be displayed for your attention.

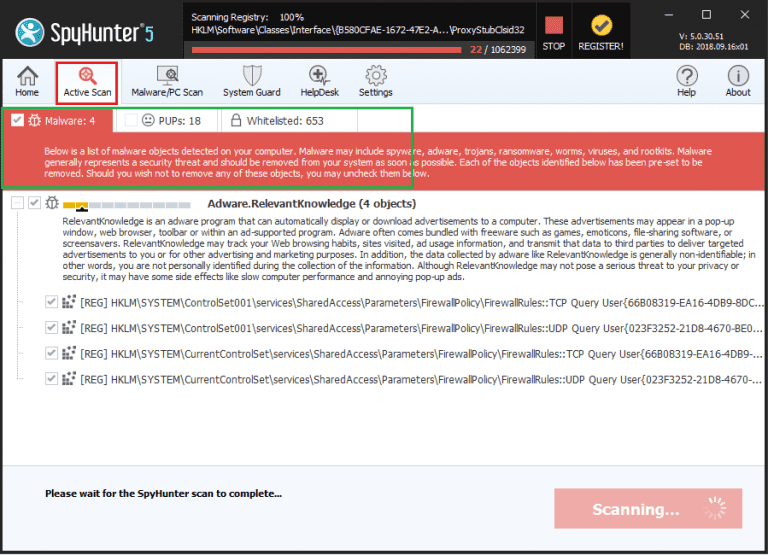
Step 7: Additionally, the scanner will initiate a comprehensive scan of your computer to identify potential threats within your device. Throughout the scan, it will present you with information such as the detected threat’s name, security level, and specific details about the threat. Relax and wait for the scan process to conclude.
Step 8: Upon completion of the scan, press the “Next” button to continue the process.
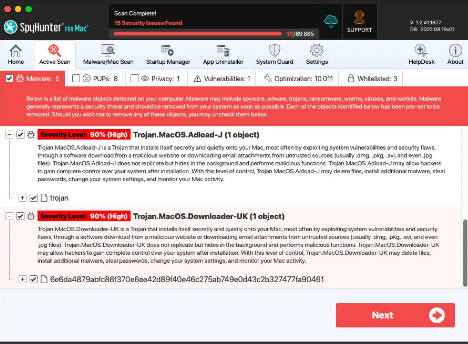
Step 9: To finalize the removal process, the application will prompt you to purchase its licensed version. Alternatively, you have the option to opt for a 7-day free trial, during which the software will be fully operational, allowing you to eliminate all identified threats.
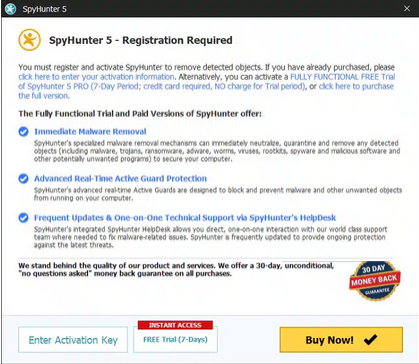
Special Offer
In order to remove Jazi Ransomware hassle free, we suggest you to scan the PC with powerful SpyHunter antimalware scanner. The fully functional free Trial of SpyHunter is Available for 7 days (Windows Version) with Credit Card required. There are no upfront charges within this period. Further, no charge will apply if you cancel 2 business days before the trail ends. For Mac Users, it is suggested to use Combo Cleaner which is a powerful antivirus and System optimizer.
Do make sure to read SpyHunter’s EULA and Privacy Policy. Spyhunter free scanner downloaded just scans and detect present threats from computers and can remove them as well once, however it requires you to wait for next 48 hours. If you intend to remove detected threats instantly, then you will have to buy its licenses version that will activate the software fully.
By following these steps, you take a proactive approach to neutralize the impact of Jazi Ransomware. Going offline disrupts its communication channels, accurate identification helps tailor removal strategies, isolation prevents further spread, and robust removal tools ensure effective eradication. Remember, the goal is to leverage technology to safeguard your systems and restore them to their optimal, secure state.
How to Recover Files Encrypted by Jazi Ransomware

In recent times, most of the ransomware attacks are linked to Djvu variants. If you’ve become a victim and seek to recover your files, this solution may be beneficial for you. STOP/Djvu ransomware has two versions: old and new. The old version encrypted data using a hard-coded “offline key” when the infected device lacked an internet connection or when the server was unresponsive. A tool by cybersecurity researcher Michael Gillespie could decrypt data affected by the old version. However, with the introduction of a new version in August 2019, the encryption method changed, rendering the old decrypter ineffective and unsupported.
For those hit by the older version, there’s hope. Emsisoft, in collaboration with Michael Gillespie, developed a tool supporting 148 Djvu variants. Victims can find more information, download links, and decryption instructions on Emsisoft’s official page.
A unique service by Emsisoft allows victims, specifically of Djvu variants before August 2019, to decrypt data if they possess a pair of the same file before and after encryption. Victims need to upload an original and encrypted file pair to Emsisoft’s Djvu decryption page. After uploading, they can download the decryption tool (provided after file upload). However, the file processing might take some time, so patience is crucial. It’s essential to note that an uninterrupted internet connection throughout the decryption process is necessary for its success.
It’s crucial to understand that STOP/Djvu ransomware doesn’t lock the whole file; it only encrypts a part at the beginning, making it unusable. Luckily, sometimes it’s possible to recover the unencrypted section. This is especially handy for audio/video files, as even if the starting part can’t be restored, you can still use most of the file.
In short, if you’ve fallen victim to Djvu’s older version, there’s a chance for recovery using tools from cybersecurity experts like Michael Gillespie and Emsisoft.
Recover Files Encrypted by other Ransomware Variants

When faced with the aftermath of a ransomware attack, there are alternative methods to recover your locked data. One such method is utilizing Volume Shadow Copies, and here’s a simple explanation along with other recovery options:
- Volume Shadow Copies: Many operating systems, like Windows, automatically create backups known as Volume Shadow Copies. These copies capture snapshots of your files at different points in time. If your files are encrypted by ransomware, you can restore them to a previous, unencrypted state using these shadow copies.
- Data Backup: Regularly backing up your data is a proactive measure against ransomware attacks. If you have a recent backup stored on an external device or a secure cloud service, you can restore your files without yielding to the ransom demands.
- File Version History: Some operating systems maintain a version history of files, allowing you to revert to a previous version. This feature, if enabled, can be a lifesaver in recovering unencrypted versions of your files.
- Consult Cybersecurity Experts: In complex cases, seeking assistance from cybersecurity professionals or specialized firms might be necessary. They may have advanced tools and techniques to recover data or provide guidance on the best course of action.
- File Recovery Software: If the previously mentioned methods fail to recover your compromised data, consider trying the Stellar Data Recovery tool. This highly effective software employs a system scanning and recovery algorithm. It searches your system partitions to locate original files deleted, corrupted, or damaged by malware. Crucially, refrain from reinstalling the Windows OS, as doing so may permanently delete “previous” copies. Before using the recovery tool, clean your PC to remove the ransomware infection. Leave the locked files untouched and follow the provided steps to enhance the chances of successful data recovery. However, success depends on the extent of encryption and overwriting.
Remember, prevention is the best defense against ransomware. Regularly update your operating system and security software, be cautious with email attachments and links, and educate yourself about potential threats. In the unfortunate event of an attack, having a combination of recovery options, including Volume Shadow Copies and backups, can increase your chances of restoring your valuable data without succumbing to ransom demands.